It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news. Bohemia popped up post-Hydra takedown and brings a fresh vibe—drugs (weed, pills, some coke) and digital goodies like hacked logins, no exact listing count, but it’s growing fast.
- The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones.
- No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
- Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
- It also includes a dark web monitoring feature that crawls the dark web and alerts you if your details show up anywhere.
- In 2025, only a few markets stand out for their security, reliability, and vendor quality.
Silk Road (marketplace)
Bitcoin is also supported, and there are multiple payment methods similar to Escrow, so both the buyer and the seller are protected during the transactions, and nobody is ripped off by the other party. It’s no wonder this is the top of many black-market websites list around the internet. If you’re planning on selling anything on Dream Market, it’s easy to create an account, and Dream Market will take 4% of all your earnings as a commission fee. The site is nicely laid out, there are a few categories to explore, and it’s quite a quaint experience.
Darknet Threat Monitoring With KELA
- This trove of stolen data included names, addresses, Social Security numbers, and phone numbers, leaving millions of individuals vulnerable to identity theft.
- Meanwhile, Facebook also offers dark web access to their social network.
- Prior to Keeper, Darren served as an advisor to JiWire, now called NinthDecimal.
- Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously.
- In fact, it helps organizations with valuable threat intelligence so that they can stay ahead of the ongoing threats.
- Our platform ensures that your brand stays one step ahead of cybercriminals, giving you peace of mind in an increasingly complex digital landscape.
“Operation RapTor shows that the dark web is not beyond the reach of law enforcement,” said Head of Europol’s European Cybercrime Centre, Edvardas Šileris. “Through close cooperation and intelligence sharing, officers across three continents identified and arrested suspects, sending a clear message to those who think they can hide in the shadows. Europol will continue working with our partners to make the internet safer for everyone.”
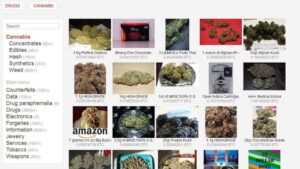
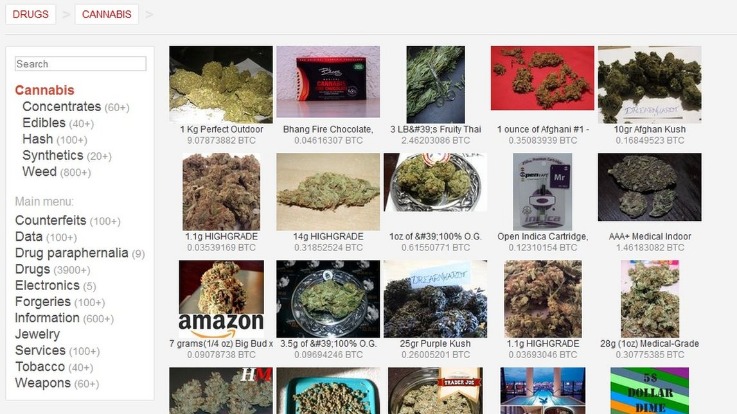
Top 7 Dark Web Marketplaces
The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search. For those venturing to the shadier side of the web or those who just want to know their identity is safe, dark web monitoring tools and identity theft protection are a must-have. One of the most common types of illicit goods is stolen login credentials, often collected from data breaches. These “credential dumps” allow criminals to access online accounts, steal identities, and commit fraud.
What Is The Dark Web? How To Access It Safely?
In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky. We’ll also discuss examples of major marketplaces, myths about the dark web, and tips on staying safe in case your personal data ever ends up there. There are a lot of misconceptions about the dark web online and in popular media. When most people refer to the dark web, they are thinking about dark web/darknet marketplaces (DNMs). Monitoring active marketplaces offers early access to malware kits, credential dumps, and fraud tools. Tracking vendor migration—such as from Archetyp to Exodus—provides insight into tactical shifts.
Bonus: The Silk Road

Onion sites are websites on the dark web that use the “.onion” top-level domain instead of “.com,” “.net,” “.gov,” etc. Onion sites use The Onion Router (Tor) software to encrypt their connections and enable anonymous communication. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust.

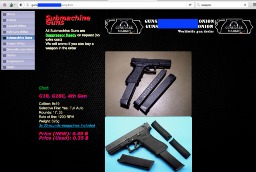
Fraud And Hacking Services
The homepage includes options like browsing products, searching, mixer, and coin exchange. You need to register first to purchase products from this marketplace. The marketplace has several rules that every user is bound to follow. If any user is found not complying with the law, strict and immediate action will be taken against them. It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoins to keep you anonymous on this marketplace. World Market is another largest dark web shops that deals with various goods and services.
However, the website has some security risks, and users experience glitches. The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. It’s a user-only marketplace, meaning you need to register to enter. During our tests for the research, we were able to register with a bogus email and a random username. All that one can expect from a deep web marketplace when it comes to anonymity and security.

BBC Tor Mirror
Perhaps the strategy should include a remediation process when exploits are detected during the monitoring. As much as it might seem a challenging task to implement, the overall benefit is worth it. In fact, it helps organizations with valuable threat intelligence so that they can stay ahead of the ongoing threats. Nevertheless, a lot of things happen in the dark web social hubs; it’s shady and illicit business most of the time, but interestingly, very active. Also, the forum served as a promotional as well as recruitment platform, whereby malicious actors and other ransomware groups use it to expand their visibility, bolster reputations, and exchange ideas.
He loves covering topics about VPNs, online privacy, and anonymity and shares his knowledge of online security with internet users through his words. Dark.fail is an easy-to-use .onion platform equipped with a status checker that tracks website uptime. The site offers access to PGP-verified URLs and runs free of JavaScript or tracking. This platform’s library of websites currently totals 50, which may not sound impressive until you consider that all the links are active and popular.
How To Stay Safe On The Dark Web
Tor Links is a backup directory of “.onion” sites in case other directories go offline. The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. They’re tightening security and carefully screening anyone who wants to join. This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk.
The forum focuses mainly on credit card fraud, but it also covers other topics such as hacking, cracking, and several other aspects of cyber scams and IT. The forum features a selective membership process, which has earned it a reputation as the best place for seasoned hackers where they can easily exchange knowledge. Besides, its expertise database expands constantly and covers hacking methods and tools that threat actors can use. FreeHacks is yet another Russian-based administrator-owned dark web community forum that offers an extensive database of hacking resources and tools. The platform focuses primarily on DDoS attacks, carding, and several other forms of cybercrime. Besides, it has a huge and highly active user community that discusses credential lists, hacking tools, email and password combos, vulnerable software, and several other things.