
– Look for a substantial number of feedback and ratings to ensure a more accurate assessment of the vendor’s performance. Additionally, it’s crucial to stay informed about the dark web’s evolving tactics and trends to mitigate risks effectively. This gives security teams time to adjust their defenses before new techniques become widespread. Early detection enables your security team to prevent a transaction, minimizing the risk of a chargeback. I can’t stress this enough, your point-of-sale systems should never share a network with general-purpose computers or IoT devices. Instead of storing actual card numbers, each card should be converted into a unique token.
Businesses that fall victim to carding attacks may suffer reputational damage, eroding consumer trust and loyalty. On the contrary, the dark web is also used for legitimate purposes, with journalists, whistleblowers, and social or human rights activists often using it to communicate securely. From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid. To ensure larger reach, the crooks distribute the collection via a clearnet domain and on other hacking and carding forums.
Infamous Dark Net Carding Site UniCC To Close
Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. Darknet markets — also known as cryptomarkets — provide a largely anonymous platform for trading in a range of illicit goods and services.

This underground economy poses significant risks to individuals and financial institutions alike. In this shadowy realm, hackers can obtain credit card details through various means, including phishing campaigns, malware attacks, and data breaches. These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases.
Financial Crime In The Shadows Of The Dark Web
According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards. The fraudulent credit cards were used to purchase gift cards, flights, hotels stays, and other goods and services. These aren’t just random forums, they’re organized platforms where stolen card data gets packaged and sold as “fullz” (full card details including CVV) or “dumps” (raw magnetic stripe data). Crucially, she also outlines what service providers—including telcos, financial services, and insurers—can do to help protect consumers from carding in today’s shifting cyber threat landscape.
Phishing Evolves With AI And Stealth: Kaspersky Highlights Biometric And Signature Risks
When you purchase an item or service online, you may be prompted to save your credit card information to the website for faster purchases in the future. While this is convenient, it places your credit card information at risk of being exposed in public data breaches, so it’s best to never save it on websites. They are used by mid-level and highly experienced fraudsters who know how to use them effectively. Gathering resources is usually the first phase for criminals who want to commit fraud. Obtaining good quality materials is always an important part to being a successful craftsman – it is no different for those involved in carding fraud. As Figure 2 demonstrates, one of the largest dark web marketplaces, Alphabay, runs its own credit card shop as an additional feature of the site.
A Brief History Of Carding Sites
- When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces.
- These platforms often provide additional layers of authentication, such as two-factor authentication or biometric verification, ensuring the protection of your financial information.
- First is to protect the president, vice president, their families, and ex-presidents, and their second objective is to investigate criminal activity relating to financial and payment industries within the US.
- If your credit card number or other details are detected on the dark web, you will be immediately alerted, allowing you to take protective measures.
- These are often compiled from multiple sources — often from multiple breaches and other similar databases; these rarely cost more than US$100 and can contain millions of records.
Paul C Dwyer, President of the International Cyber Threat Task Force, examines the regulatory and operational questions raised by the cyberattack on M&S. Today, the technology synonymous with crimes is a tool for journalists, activists, hacktivists, and whistleblowers to share secrets while retaining their anonymity. Prices can vary significantly based on the quality and validity of the card information, ranging from as low as $5 to several hundred dollars.
Identity theft and fraud protection for your finances, personal info, and devices. These listings include screenshots of the check, which may expose customer PII. The Darknet Market can be an unregulated market where people can buy just about anythingalmost anything. This includes firearms, illegal drugs, horrific videos, fake passports, Netflix accounts, credit cards, or even the rental of the hitman. These sites may offer stolen credit card numbers, CVV codes, expiration dates, and even personal identification details. For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110.
Cool Augmented Reality Examples To Know About
Physical cards are usually cloned from details stolen online, but can be used to withdraw from ATMs. Because the merchant requires equipment to clone the card and must send the buyer a physical product complete with PIN number, the price for cloned cards is much higher. It’s worrisome to know that a criminal could steal your credit card information and sell it on the dark web. Remember that even if you are a victim of fraud, federal law limits your liability to no more than $50 of unauthorized charges.
Antivirus Software
It has a bidding feature, with new batches of stolen data being frequently added. One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. Most users on the Dark Web are logged into a Virtual Private Network (VPN) to further conceal themselves.
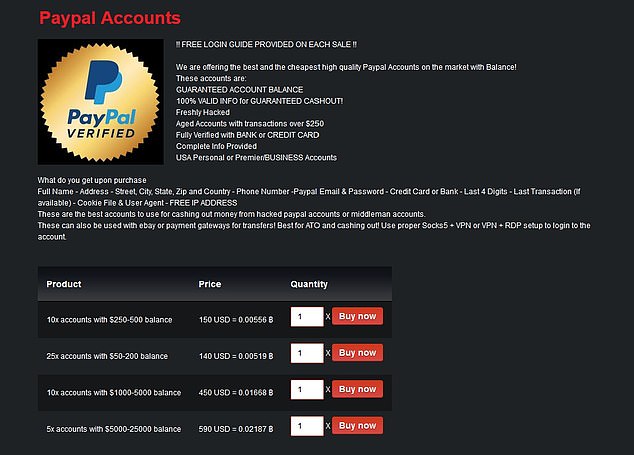
Russian Group Releases Stolen Credit Cards On Dark Web Here’s How To Protect Your Credit From Criminals
- More than 9,000 active vendors selling fake IDs and credit cards reported sales in the several thousands.
- If you’re connected to a public WiFi network, avoid making any purchases online while you’re connected to the network as this could place your financial data at risk.
- The Threatpost editorial team does not participate in the writing or editing of Sponsored Content.
- Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025.
- In a classic example, the surface web can be imagined as the tip of a large iceberg whose bulk remains hidden just under the surface.
This often includes a “checker service,” a compromised merchant account they use to run dinky charges through to see if the card is still valid, Krebs says. If someone agrees to use the shop’s checker service instead of a third party, the shop will give a guarantee that at least a portion of the cards are usable for a certain period of time. Credit card details can be sold as digital items on the dark web, with the basics costing around $17.36. Physical cards, on the other hand, are cloned from stolen online details and can be used to withdraw cash from ATMs.
The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them. Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage. The price for cloned cards varies depending on the credit limit, with an average price of $171.
It provides them with valuable information needed to carry out a variety of attacks. The best way to monitor your credit cards is by downloading your credit card company’s app from the Apple App Store and Google Play Store. While we have not yet understood how the BidenCash criminal site obtained this volume of active debit and credit cards, it is one of the most serious menacing underground data enterprises in the world. A criminal site known as BidenCash, which uses the president’s name and likeness to trade in stolen data, has just leaked 2,165,700 credit and debit cards online. Research by BitDefender has revealed the common prices for a range of illicit goods, from credit cards to credentials databases and more. Strong passwords and Multi-Factor Authentication (MFA) help keep your online accounts secure from compromise.



