Accidental leaks at the Tor entry nodes can potentially expose your IP address. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. Also, use an effective antivirus program to check threats if you decide to download files. You can check out this guide on the best antivirus software applications today.
- The secret club which keeps illegal content hidden, using encryption and anonymisation tools.
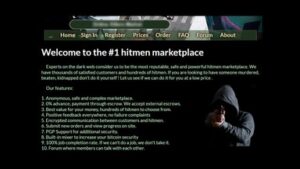
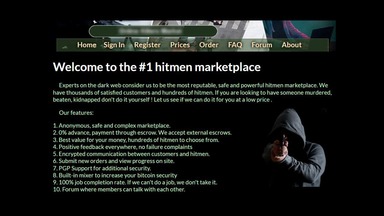
- You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers.
- Many CSPs are based in the US and may be obtained through Mutual Legal Assistance (‘MLA’, see below).
- This feature is particularly useful for individuals living under oppressive regimes, as it allows them to communicate and access information without fear of surveillance or retribution.
- Data gleaned from ransomware and data breaches is available on the dark web.
- Our expert industry analysis and practical solutions help you make better buying decisions and get more from technology.
Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. To expand their reach, some marketplaces established parallel channels on Telegram. This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself. The fact that it’s also used for benign and legitimate reasons also presents an argument to not limit its availability. Tor and the deep web enables people to anonymously access information and resources unavailable to those who live in authoritarian governments, for example, or those in war-torn countries such as Ukraine.

Top 6 Dark Web Telegram Groups And Channels In The UK
- For example, in cases of ‘honour’ based violence and forced marriage, threats to post personal information on social media can be used to bring shame on victims in order to silence and coerce.
- However, you should be aware that accessing the dark web can expose you to various risks, including malware, phishing attacks, and illegal content.
- Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor….
- Sections of the dark web are often closed down too, as part of police operations.
- About nine months ago while researching a story, I found myself added to a large Telegram channel which was focused on selling drugs.
By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Understanding the dark web, including safe navigation with the Tor Browser, is crucial for anyone interested in internet privacy and security issues, highlighting the balance between anonymity and the potential for misuse. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web. Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information.
“Once he had stolen the cryptocurrency, Paul Chowles sought to muddy the waters and cover his tracks by transferring the Bitcoin into mixing services to help hide the trail of money. As part of the investigation team working on the case, Chowles took the lead in the analysis and extraction of relevant data and cryptocurrency from the devices seized from White. A former National Crime Agency officer has been jailed for stealing and hiding 50 Bitcoin – now worth £4.4m – which had been seized as criminal property during an investigation into online crime on the dark web. My old email address’ path to the dark web is one that may be familiar to my fellow millennials.
Organisations Must Prepare Now For New Fraud Prevention Law
Here in Manchester, a gang of five university students were recently sentenced for selling more than £800,000 worth of drugs on the Dark Web to customers in Australia, Europe, New Zealand and the United States. Because we must be in no doubt, the cyber sphere is where modern day crime is being committed and international conflicts played out. But nor would they have anticipated the darker side of technology that would become apparent, or the threats that it poses.

UK And The Dark Web – Here’s How To Check If You’re On There
In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces. The users of the dark web are typically aiming to block governments from snooping on them. This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above. Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs.
What Is The Dark Web? Here’s How To Access It Safely (and What You’ll Find)
We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. If you have been arrested for accessing illegal websites on the dark web, our criminal defence solicitors are on hand to lend their expertise. For gamers, even buying a skin for their in-game character using their parents’ saved credit card details without consent would be a violation of the CMA. Using off-the-shelf tools to perform DDoS attacks, for example, or accessing a protected server are other common examples of these low-level offenses.
Illegal Activities:
If personal data such as your National Insurance Number, bank details or passwords are found on the dark web, take immediate action to protect yourself. Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorised activity, and consider enrolling in a credit monitoring service. Additionally, report it to Action Fraud, the National Fraud & Cyber Crime Reporting Centre for further protective measures. The dark web and the browsers used to access its sites are not illegal. Alongside the bad things are lots of normal online communities and social networks which break no laws. It is also a space where people, such as journalists, who hold sensitive information, can share it while shielding their identities.
Identity theft is yet another sinister consequence of data exposure on the dark web. Criminals can assume another person’s identity, leading to devastating consequences for the victim, including ruined credit scores and reputation. But don’t worry, you can still access Telegram in the blocked countries by simply using a VPN or a proxy. The Code for Crown Prosecutors is a public document, issued by the Director of Public Prosecutions that sets out the general principles Crown Prosecutors should follow when they make decisions on cases. The use of two different components to verify a user’s claimed identity.
Caution: Safety Comes First When Visiting Dark Web Links
Other illegal services like selling documents such as passports and credit cards also require an infrastructure that guarantees anonymity. The same can be said for people who leak other people’s personal information like addresses and contact details. Although, this depends on the country you’re in, as totalitarian regimes are obviously against platforms that provide anonymity to users. It is used by whistleblowers, the US military, journalists, and even those simply seeking rare items — out-of-print books, for example.
What Services And Tools Are Available On The Dark Web?
However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events. It will offer you an additional layer of encryption to access the deep parts of the internet. And just yesterday this government launched a new world-fist £13.5 million Cyber Innovation Centre in London to help secure the UK’s position as a global leader in the growing cybersecurity sector. And then there’s the Dark Web where anonymity emboldens people to break the law in the most horrifying of ways with platforms that enable dangerous crimes and appalling abuse.

The Price Of Your Data On The Dark Web

In instances where an individual offers fake identity documents online, prosecution should also be considered under the Identity Documents Act 2010, where the document is one prescribed under section 7. The CMA 1990 deliberately does not define what is meant by a ‘computer’, to allow for technological development. So too are some of the criminals on the Telegram groups I am now a member of, with FreeDurov imagery being shared in English and Russian widely. French authorities noted in their statements about Mr Durov’s charges that police there and in Belgium had historically an “almost total lack of response from Telegram to legal requests”.

Learn how to gather dark web OSINT using tools like DarkSearch, SpiderFoot, and Maltego. However, it is essential to be cautious because it can be a risky place. Moreover, use it only for ethical and legal purposes to avoid legal consequences on the Dark Web.
Trend Micro specialists constantly monitor the internet, particularly the dark web, for leaked data. Once such data is identified, it is validated and ingested into Cyber Risk Exposure Management. When you register a domain in Trend Vision One, a scan is performed to verify whether the domain user data has been compromised by a leak—with historical data back to 2010. Afterward, Cyber Risk Exposure Management performs additional scans on a weekly basis. The Dark Web relies on darknets or networks where connections are made between trusted peers. Examples of Dark Web systems include TOR, Freenet, or the Invisible Internet Project (I2P).
Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. In due course, the framework was remodeled and made public as a secure browser. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. With the onion browser, you can access ordinary HTTPS websites on the web. This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity.