To minimize the risk of exposure, dark web insiders take precautions to cover their tracks and conceal their involvement in illegal activities. This involves laundering the proceeds from insider trading through multiple cryptocurrency wallets and transactions to obscure the funds’ origin and destination. Furthermore, dark web actors may adopt the use of “mixers” or “tumblers,” which are services that mix different users’ cryptocurrency transactions to obfuscate the flow of funds. These techniques make it difficult for authorities to trace the illicit transactions back to the perpetrators, providing an added layer of protection for dark web insider traders.
Admin Of The Internet’s Only Insider Trading Forum Speaks Out
Dark web marketplaces like Silk Road paved the path for the early use of cryptocurrencies in the illegal exchange of goods and services. As cryptocurrencies gained popularity, financial crimes committed on the dark web, such as insider trading, became more intricate and sophisticated. On the dark web, insider trading is significantly facilitated by hackers. Cybercriminals target businesses in order to break their security measures and obtain private data. Then, before the information is made public, the stolen data is traded on dark web forums or used to carry out profitable trades. The deep web refers to the part of the internet that is not indexed by search engines and requires authentication to access, such as password-protected websites and databases.
Simply put, accessing and browsing the dark web is perfectly legal. For example, it maintains your privacy and enables you to access untraceable content and services. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.

Explore Content
- Despite these closures, new platforms continuously rise, adopting advanced security measures to evade detection.
- The market is also known for its listings related to financial fraud, such as phishing tools and stolen credit card information.
- The number of market-U2U and market-only buyers also drops as a consequence of operation Bayonet.
- It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting.
- We find that trading properties of buyers and sellers reflect the dominance of DWMs in the ecosystem.
- By allowing large blocks of stock to be traded without revealing the details of the transaction, dark pools can help prevent sudden price movements that could be triggered by a large trade.
The increased trading activity driven by the availability of dark pools dilutes the proportion of informed trading in the overall market, leading to a fall in the risk of adverse selection faced by uninformed traders. The informed traders’ migration to the dark pool would result in uninformed traders leaving the erstwhile safety of the dark pool for the lit exchange. This would, in turn, lead to an overall loss of trading activity in dark pools and a net gain by lit exchanges. When informed traders trade with their information, they help the market to discover the ‘fair’ price for the asset they trade. This self-selection improves price discovery under normal conditions. Dark trades are facilitated by ‘dark pools’ – a growing class of platforms that do not offer pre-trade transparency.
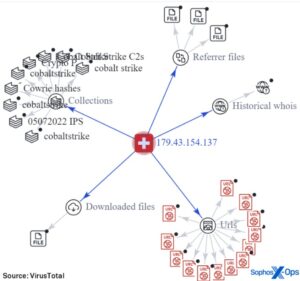
Russian Market
To protect against the threats posed by the dark web, businesses must adopt a proactive and multi-layered cybersecurity strategy. These measures are essential for safeguarding sensitive data, maintaining regulatory compliance, and mitigating risks effectively. Another reward of insider trading on the dark web is the networking opportunities it provides.
The resulting data set includes for each transaction the source and destination entities, the time, and the value of the transaction. The largest component of the S2S network of U2U transactions between sellers for each year with the respective number of nodes (N). The nodes are sellers that are active in that year, and an edge is placed between two sellers if at least one transaction occurs between them during that year.
Helpful Links
Despite these closures, new platforms continuously rise, adopting advanced security measures to evade detection. The dark web, an enigmatic subset of the internet, operates as an encrypted and anonymous network inaccessible through standard web browsers. Unlike the surface web, which is indexed and easily searchable, or the deep web, which houses private databases and unindexed content, the dark web is a haven for covert activities. It facilitates a range of illicit trades, including the sale of stolen data, hacking tools, counterfeit documents, illegal drugs, and firearms. A dark web market is a hidden online platform where users can anonymously buy, sell, and trade illegal or sensitive items.
#BHUSA: Microsoft Debuts AI Agent Able To Reverse Engineer Malware

Businesses face substantial cybersecurity risks due to the proliferation of these marketplaces. Data breaches often lead to sensitive corporate information appearing on the dark web, which can fuel further attacks. A security gap analysis can help businesses identify vulnerabilities that hackers exploit to compromise their data. Additionally, investing in cybersecurity services for small businesses ensures stronger defenses against threats originating from these illicit platforms. The dark web is part of the deep web, inaccessible via standard browsers.

Staying Safe On Abacus Market
Perpetrators have likely migrated to more secure encrypted channels instead. For starters, dark web traders can use their access to financial data to identify and capitalize on potential discrepancies between the current market price and the future price of a given asset. Through the use of software programs and custom algorithms, traders can analyze patterns and determine whether or not there is an opportunity for profit. Additionally, by understanding how certain companies’ stocks move, traders can use their insights to trade in a more informed manner. Insider trading has long been a topic of interest in the world of finance, but many are unaware of the potential uses of dark web insider trading. With its anonymity and lack of oversight, the dark web is an ideal place to acquire valuable information and make money off it.
Beyond Basics: The Real ROI Of Cybersecurity Education
The use of the dark web raises suspicion as it shows there is something you want to do privately. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer.
With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. It is easily accessible by the general public and requires no special configuration. You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data.
Some users also share links on encrypted apps like Telegram or Keybase that you can check. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. It is the dark web’s version of Wikipedia with a massive links directory.

We consider the whole ecosystem, i.e., all markets and the U2U network. In panels (b, c), we show the number of all sellers and buyers per quarter, respectively. In panels (d, e), we show the median net income in USD of all sellers and buyers per quarter, respectively. In panels (f, g), we show the PDF of the total money received by each seller and the total money sent by each buyer, respectively. Conversely, transaction networks obtained from the blockchain contain the entire transaction data of the DWMs and U2U transactions, allowing a thorough investigation of the ecosystem as a whole.