
Created by Troy Hunt, an Australian web security consultant, it discloses whether your login credentials and personal and financial data have been stolen or leaked online. DarkOwl is a leading darknet company that provides the largest commercially available database of darknet content worldwide. Part of the DarkOwl product is Vision UI, which enables users to monitor, search, and analyze the dark web and provides real-time threat intelligence. Tor (The Onion Router) is a free and open-source dark web browser that enables anonymous communication by routing Internet traffic through a volunteer network of over 6,000 relays. The Tor Browser opens access to “.onion” sites, unique addresses within the dark web.

What Is Software Deployment: Risks And Best Practices
To safeguard your information, avoid sharing personal details or engaging with unverified platforms. By staying vigilant, you can enjoy the benefits of deep web exploration while maintaining your cybersecurity. Kilos is a powerful deep web search engine designed for users seeking comprehensive access to the invisible web. It stands out for its extensive index, which includes over 553,994 forum posts, 68,860 listings, 2,844 vendors, and 248,159 reviews. Kilos allows you to search across six major dark web marketplaces, offering a broader scope than its predecessor, Grams. To use NotEvil effectively, start by accessing it through the Tor browser for maximum anonymity.
Cyber Incident Response Maturity Assessment
– Vulnerabilities are where security vulnerabilities in popular software used in many companies are sold. – Exposed Leaks, names, email addresses, and precision assets related to your organization are usually sold in dark web markets. Dark web forums are online communities where individuals participate in discussions on a wide range of subjects, from technology and privacy to more illicit matters. Since activists, journalists, and advocates need the dark web to communicate securely, find evidence, and bypass censorship, it remains a tool for privacy and free expression. A key feature of DuckDuckGo is its strict no-log policy, ensuring user privacy. Nevertheless, the company estimates its user base to be around 25 million individuals.
What Are Some Popular Dark Web Search Engines?
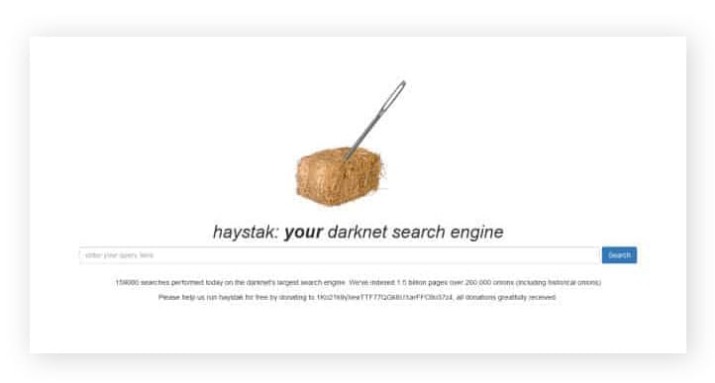
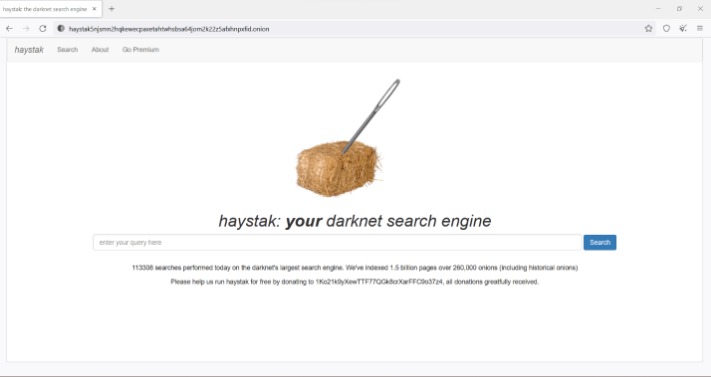
Many deep search engines prioritize user privacy, but not all of them offer the same level of security. This makes it crucial to choose search engines with robust privacy protection features. Haystak is one of the best search engines for dark web exploration, boasting an impressive index of over 1.5 billion .onion pages. This extensive database makes it a reliable tool for searching hidden services and uncovering a broad range of invisible web content. Haystak offers both free and premium search options, allowing you to choose the level of access that suits your needs.
Dark Web Monitoring Tools
These search engines catalog .onion domains, which are not easily accessible from regular web browsers. These top 10 dark web search engines are important for research, evidence collection, finding hidden resources, intelligence, and various other resources that are not easily accessible. Each module surfaces actionable intelligence, letting you prioritize your response based on business need and risk, minimizing response time and facilitating efficient remediation. Mandiant Digital Threat Monitoring offers visibility into intelligence pertaining to threats and leaked credentials or other corporate secrets on the open internet or the dark web. This intelligence data is bolstered by context delivered through machine learning, driving relevant, prioritized alerts that facilitate the triage process.
However, the dark web also supports privacy-focused communities, whistleblower platforms, and other legitimate services. No, many .onion sites serve legal and ethical purposes such as secure communications, anonymous sharing, and journalism support. Yes, platforms like DeHashed, LeakLooker, and DeepPaste provide access to data breaches and leaked credentials. However, engaging in illegal activities on the dark web is strictly prohibited. The service also protects the brands and reputation of customers by scanning all websites for harmful content about those companies.
Search Cyberogism
Always cross-check the information you find, especially when accessing academic or investigative resources. For added security, use a VPN alongside the Tor browser to protect your identity. Dark web search engines are designed to make it easier for users to access websites and information on the dark web. These crawlers provide access to sites that cannot be accessed by normal search engines. The deep web includes all websites and pages that are not indexed by search engines and are not publicly accessible.
Phishing campaigns on the Dark Web target unsuspecting users to steal credentials and sensitive data. With Brandefense’s Threat Intelligence, organizations can identify and neutralize phishing threats proactively. Osint sources include newspapers, magazines, news, conferences, photographs, videos, social media accounts, blogs, press conferences, and academic documents. With the spread of the Internet and the increase in the use of social media, there has been a significant increase in OSINT sources. The point to be considered is collecting information from resources that do not require contact with the target.

Onion City
Always use a VPN, verify links, and stick to legitimate purposes to minimize risks. They often have smaller indexes (e.g., Ahmia’s ~10,000 sites) and may include ethical filtering to block illegal content, but they lack features like personalized ads or real-time updates. Machine learning is transforming dark web search engines, with Haystak already leveraging AI for result ranking and spam detection. By 2027, engines like NotEvil could adopt AI to enhance community-based filtering, identifying abusive content with greater accuracy. Users relied on handwritten lists or email chains to share .onion links, with no centralized indexing. The lack of search tools made the dark web a fragmented, insider-driven space, inaccessible to most.

This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design. By 2030, ethical debates over content moderation could split the ecosystem, with some engines (e.g., Torch) remaining unfiltered and others (e.g., NotEvil) adopting stricter policies. Users will need to navigate this divide, favoring open-source tools for transparency. NotEvil could integrate differential privacy techniques to share aggregate data, aiding researchers studying dark web trends.
- Operating on a freemium model, users have the option to upgrade for an ad-free experience and access to features like historical website versions.
- This makes it a great choice for beginners exploring the invisible web for the first time.
- Keep your software always up-to-date, exercise extreme caution when clicking on links or downloading files, and avoid sharing personal information.
- Monitor and prevent security incidents against your suppliers, people, and brand with actionable alerts from the Dark Web.
- The tool can also help you mitigate future risks by providing deeper security visibility with rapid monitoring.
Malicious And Scam Sites
- By staying vigilant, you can enjoy the benefits of deep web exploration while maintaining your cybersecurity.
- You can browse through actual newspaper clips for any topic in a timeline spanning the entire 20th century.
- Use specific keywords to refine your search results and avoid wasting time on irrelevant pages.
- If it’s to find library books or look through old newspapers, it definitely has its benefits.
- Dark web engines like NotEvil index these domains exclusively, allowing keyword-based discovery of sites that surface engines can’t reach.
- While not Evil does not claim divine authority, it relies on user feedback to identify and address problematic links or hosts.
Cobwebs Technologies is a leading global security and intelligence provider transforming web intelligence’s face. This dark web monitoring tool enables seamless analysis of publicly available data resources available on the darknet. Part of its service is the threat intelligence solution that automatically scans and updates the databases with new information collected all around the web. This tool monitors extensive dark web resources for exposed credentials, intellectual property, fraudulent activities, stolen data, VIP and executive threats, and more.
CISOs Brace For Supply Chain Attacks With Proactive Attack Surface Monitoring
To explore the hidden web safely, the Best Dark Web Search Engines for the Tor Browser provide a way to find onion sites without exposing your identity. Yes, OnionLand is a dark web search engine that allows you to search through forums and other hidden .onion content. OSINT helps cybersecurity professionals gather publicly available intelligence—often from hard-to-access sources like the dark web—to predict, prevent, and respond to threats.
TorlanD opens up access to a vast range of hidden content, allowing you to navigate the deep web freely without restrictions. It provides unrestricted and uncensored search results, allowing access to a wide range of hidden content. The dark web is a double-edged sword, offering anonymity but also posing significant risks.



