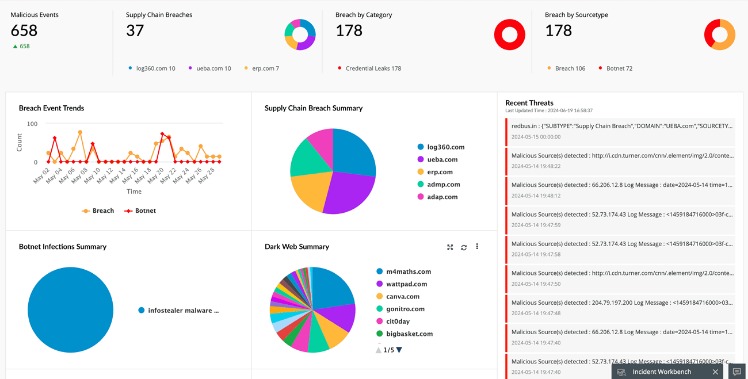
You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. Despite the sinister name, the Dark Web is only one part of the overgrown internet that is much larger than what most search engines show. To fully comprehend what is Dark Web, one has to grasp the legal and illegal personas, legitimate uses of anonymity, hidden websites, and whistleblowers. B2B companies, in particular, are experiencing increasing risks to their assets from threats originating from these concealed forums and markets. Despite the fact that it can be used for anonymity, freedom of speech, and journalism, the Dark Web is home to some of the worst internet scams.
Understanding BlackCat Ransomware: Threat Overview And Protective Measures
Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more. It includes media and archives which cannot be crawled and indexed with current search engine technology. Understanding how to access the dark web is valuable for IT leaders, cybersecurity experts, and professionals who need to monitor hidden threats or preserve online privacy. By following this dark web access guide, applying Tor browser safety practices, and knowing when it’s safe to browse the dark web, you can navigate responsibly without compromising your security. Law enforcement agencies in many countries monitor the dark web to combat illegal activities.
Protecting Yourself On The Dark Web
The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information. I2P can only be used to access hidden sites that are only available on the I2P network.
BBC Tor Mirror
Tor provides users with a higher level of privacy, which is particularly attractive to threat actors, cybercriminals, hackers, and government operatives who want to keep their identities secret. Safety concerns on the dark web include encountering criminal-run websites offering illegal goods and services, with the added risk of exploitation and theft. Engaging in illicit activities can lead to prosecution, as the law applies equally in this hidden part of the internet. Suspicious links and downloads pose a threat too, potentially leading to exposure to unwanted material or malware infections. Law enforcement’s presence, operating anonymously, aims to curb criminal activities, but it also underscores the dark web’s legal dangers. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web.
OnionLand Search

Despite its reputation, the dark web isn’t solely defined by illicit marketplaces or nefarious activity. Hidden networks also host a range of resources that can inform, educate, and support individuals who value anonymity. From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web. On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity.
- Malware, ransomware, and hacking tools are also readily available for purchase or rent, enabling attackers to launch sophisticated campaigns.
- The platform is protected from government interference and malicious attacks to protect the user.
- While accessing the dark web can be a fascinating and eye-opening experience, it’s important to consider the ethical implications of doing so and exercise extreme caution to avoid nasty surprises.
- While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution.
- Download and install Tor first, and optionally a VPN for added security.
Despite its relatively high profile, the dark web makes up a vanishingly small portion of the World Wide Web, perhaps less than 0.01 percent. However, if you’re looking to trade or buy something, the risk of scams increases exponentially. People often make the grave mistake of divulging their private information to the seller or anyone else who can take advantage of it and harm the user in many ways. Private Internet Access even offers the Shadowsocks proxy for added security. There’s also MultiHop that boosts your encryption, along with MACE which blocks tracking.

Dark Web Search Engine
It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings.
How To Browse The Dark Web
Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication. When accessing the dark web, the first step is to install a dark web-friendly browser on your computer. Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address. The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. The dark web is a common gathering place for hackers and other cybercriminals, which can make browsing the dark web a risky activity.
The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project. In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more.
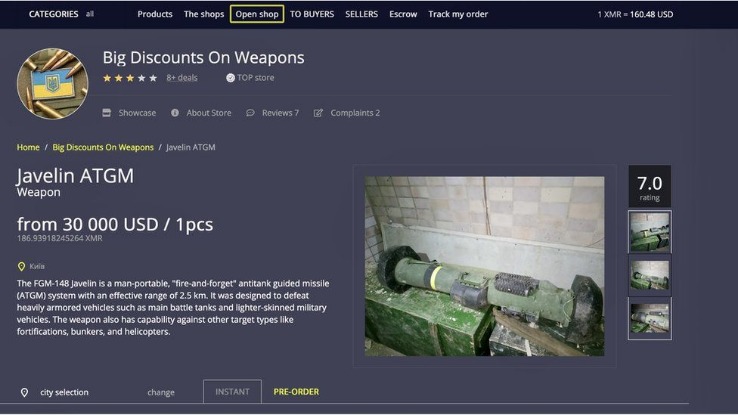
All v3 .onion addresses (the current standard) are 56 characters long and end with “d” to denote the URL version in use. Each address also contains cryptographic information that enables a dark web browser to connect to the site. That allows .onion sites to be accessible anonymously without services like DNS. To do so, enter a .onion URL and you’ll be taken to the dark web page being served at that address. From a cybersecurity perspective, the dark web is rife with risks.
Instead of ending in .com or .co, dark web websites end in .onion. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”.
In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. You can also take a look at the blogs & essays section if you want to find some nifty coding resources. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.

If you have any questions or suggestions regarding the accessibility of this site, please contact us. By embedding these standards into their security framework, organizations can minimize their exposure, fortify their defences and stay one step ahead of cybercriminals. The dark web is also home to legitimate sources of information that may not be available through traditional means. Whistleblowers, journalists and political dissidents may use the dark web to share information that would otherwise be censored or suppressed. We may earn a commission when you buy through links on our sites.©2025 GIZMODO USA LLC. The silver lining is that VPNs work on iPhones so you can mitigate the risk by connecting to one beforehand.



