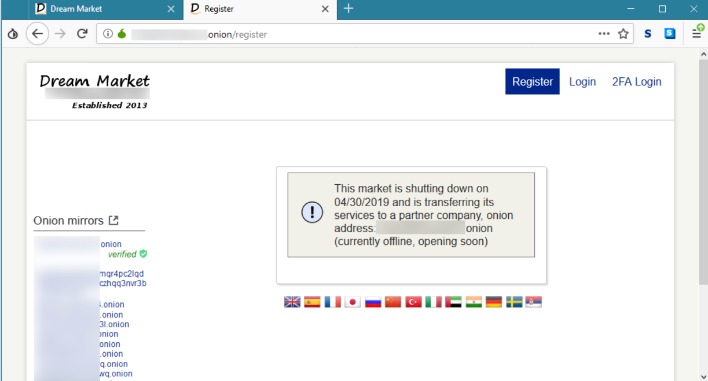
Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered. However, in the event of a dispute don’t expect service with a smile. Every communication is encrypted, so even the simplest transaction requires a PGP key. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s.
Hacking Tools And Services
Additionally, escrow services act as intermediaries, temporarily holding funds until the buyer confirms the transaction, reducing fraud risks. The Dark Web is a concealed segment of the internet that is not indexed by conventional search engines and requires specialized software, such as the Tor (The Onion Router) network, for access. While it hosts legitimate uses, such as protecting privacy in oppressive regimes, it is also infamous for facilitating illegal trade in drugs, weapons, counterfeit documents, and stolen corporate data.
Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.
Wi-Fi Security: How To Protect Your Network From
Give it a try and choose the pricing plan that will make a difference for you. The deep web is just the part of the internet you can’t find with a search engine. It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content. Just because the seller has good reviews does not mean you can trust them. There’s nothing stopping sellers from packing up and leaving the market at any time.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing. For this reason, you cannot browse through these sites using your default search engine. Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network.
- These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services.
- Hence, you never know when a popular .onion site is going to vanish, or even die.
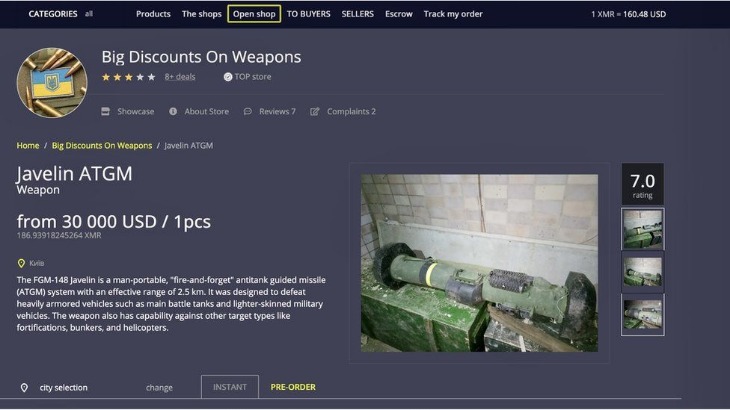
- Buying illegal substances, stolen merchandise, and counterfeit currency or goods online poses significant risks for both the buyer and the seller.
- The structural change seen in the multiseller network is not observed in the multibuyer network, as show in Fig.
- Almost any computer-literate person can enter the market according to her/his skill levels.
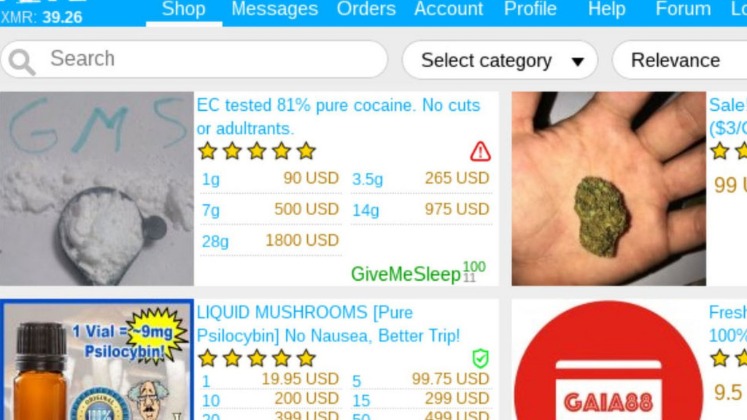
In fact, everything is in English, and the site picks up users everywhere in the world. People visit this market to buy stolen credit cards, personal data, remote desktop account credentials, and logs gathered from information-stealing malware. Buyers can enable two-factor authentication, and transactions are protected by escrow, including multisignature escrow for added safety.

Common Scams On Dark Web Marketplaces
The entire website is in Russian, but the vendors are present worldwide. It accepts payments through Bitcoin and the Escrow system and ensures that your identity remains anonymous during your purchases. By implementing strong cybersecurity measures, SMBs can comply with cybersecurity regulations and safeguard their operations from Dark Web-related threats. Despite these takedowns, modern illegal markets have evolved by adopting decentralized hosting structures and integrating privacy-focused cryptocurrencies such as Monero to eliminate traceability. Hydra, a Russian-language Dark Web marketplace, operated for years before its 2022 takedown by German authorities, demonstrating the adaptability of these underground economies.
Essential Security Tips For Using Dark-Web Marketplaces
It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. As noted by Andy Greenberg at Wired, while the deep web makes up approximately 90% of the internet, the dark web makes up only around 0.1% and is designed to provide anonymity for users and site owners. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
Why Choose Forest VPN?
All in all, it is not illegal to access the dark web, but it can create issues for you. If you don’t take the necessary measures, many unsavory activities can expose you to unnecessary risks. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities.
TOR Browser is a free, modified version of the Firefox web browser configured to connect to the TOR network. You may also use it to access the regular internet more anonymously. With proper monitoring resources, you can gain visibility into threat actors and their activities. This includes accessing restricted channels and automating intelligence gathering to anticipate attacks targeting your organization, employees, and customers. These differences aren’t necessarily clear-cut, as there are overlapping aspects between the Deep and Dark Web. Therefore, it’s likely that not all deep- and dark-web file repositories represent good intentions.
One of the most well-known technologies enabling darknets is the Tor network, which was developed by the U.S. Naval Research Laboratory in the mid-1990s and later released to the public. Tor, short for “The Onion Router,” routes internet traffic through a global network of volunteer-operated servers to anonymize a user’s online activity. This technology initially had noble intentions, aiming to protect activists, whistleblowers, and individuals in repressive regimes. However, it soon became a double-edged sword as malicious actors began to exploit its capabilities for illicit purposes.

In fact, the attacker need not even have much of any technical prowess – just a basic, high-level, abstract understanding of web attacks. Simply install TOR, find the right .onion website, pay a little BTC, choose your target and attack (DDoS and email spam, of course, being the most common), and click a button. The guides and tutorials are so well documented that a Baby Boomer who has difficulty using their printer could reasonably perform these attacks. Whatever the risk involved, some users of the Internet felt that being told what they can and cannot possess, physical or digital, was akin to oppression.
Tweak Tor Browser Settings
With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix. Even platforms like Netflix, which require paid access, are technically part of the Deep Web. However, the closure of Silk Road did not end dark web activity; it only dispersed it across other, more resilient markets. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. For several years, Yahoo was at the apex as the internet’s best web service provider, offering…
Why Is VeePN The Ultimate Online Safety Solution?
Notably, the number of buyers and sellers significantly drops after the operation Bayonet in the last quarter of 2017, which shut down AlphaBay and Hansa markets, causing a major shock in the ecosystem34. However, the number of buyers rapidly recovers, which does not happen to sellers. Normally these markets employed less reliable exchange methods like physical trade, leaving cash at one drop point and retrieving the purchase elsewhere. This was not much different from the way some black market trading had existed for centuries. The only difference at that point was just a new medium of communication, so, in general, the products remained the same. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment).



