
So, if you aspire to use Tor privately, you can use VPN or Tor gateways (Tor nodes that are not publicly indexed). While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle East and Asia countries.
Method II – VPN Over Tor
The most notorious marketplace to date was Silk Road, an online black market for drugs, which was shut down by the FBI in 2013. Despite this, similar markets have continued to emerge, fueling the Dark Web’s reputation as a haven for illegal trade. In this article, we’ll dive deep into the hidden world of the Dark Web, exploring its origins, structure, purposes, uses, risks, and the fascinating (and often dangerous) things that exist within it.
How To Access The Dark Web Safely And Securely
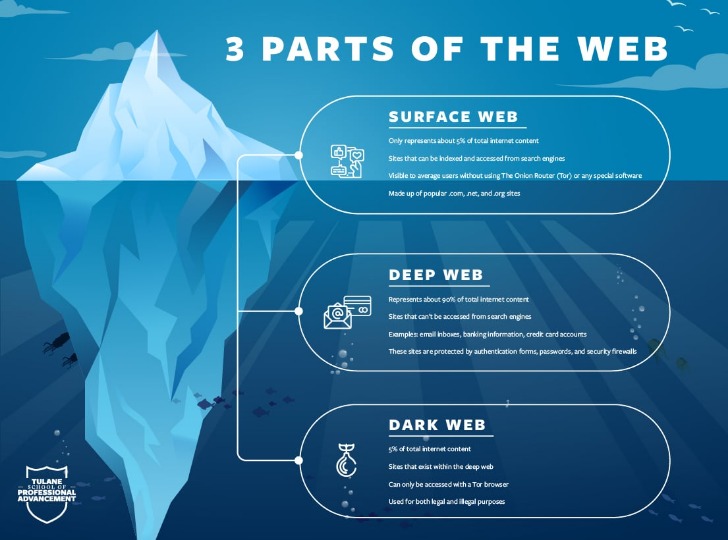
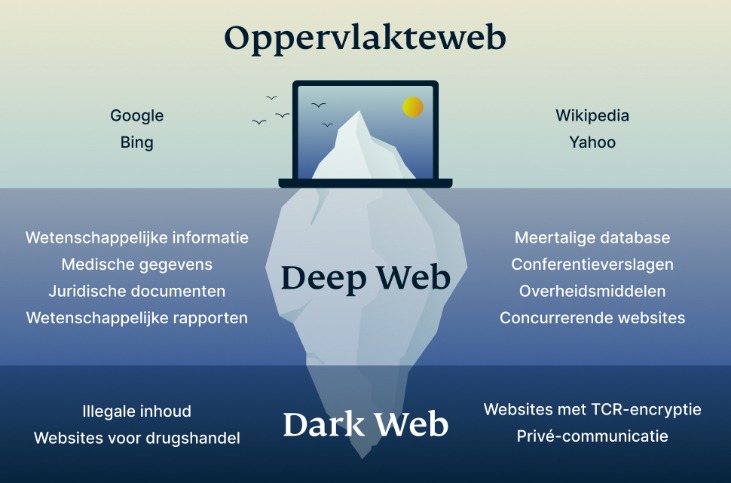
- On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines.
- For the safest experience always use a reliable firewall, and multi-factor authentication (MFA).
- We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch.
- As noted by Andy Greenberg at Wired, while the deep web makes up approximately 90% of the internet, the dark web makes up only around 0.1% and is designed to provide anonymity for users and site owners.
- But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web. As a result, you can be exposed to different malware types, including botnets, ransomware, keyloggers, and phishing. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing.
How Can Individuals Find Out If Their Information Is On The Dark Web?
Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered. However, in the event of a dispute don’t expect service with a smile. Every communication is encrypted, so even the simplest transaction requires a PGP key.
The Dark Web Vs The Deep Web
Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic. This prevents anyone—including your ISP—from knowing that you’re using the Tor network. Though the dark web offers anonymity for journalists and activists in oppressive regimes, it raises many ethical concerns. You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers.

What Is A Dark Web Scan?
It also serves a very important role for those in need of life-critical privacy. The deep web encompasses unindexed content, including databases, academic journals, subscription services, and password-protected sites like banking portals. The deep web is not inherently sinister; it simply includes all content that isn’t open to the public.
Dark Web Hub
At the dark end of the web, you’ll find the more hazardous content and activity. Tor websites are located at this far end of the deep web, which are deemed the “dark web” and are only accessible by an anonymous browser. Locating surface web websites is possible because search engines can index the web via visible links (a process called “crawling” due to the search engine traveling the web like a spider).
Risks In Accessing The Dark Web

Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. Identity theft monitoring is critical if you want to keep your private information from being misused. Passwords, physical addresses, bank account numbers, and social security numbers circulate in the dark web all the time. You may already be aware that malicious actors can use these to harm your credit, engage in financial theft, and breach of your other online accounts. Leaks of personal data can also lead to damage to your reputation via social fraud.
Many people use them for privacy and free speech, like whistleblower sites or secure communication channels. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks.
There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. Your ISP can’t see which websites you’re visiting on the dark web when you’re using Tor, but they might be able to predict or assume you are using Tor if they analyze your monitored internet traffic. Data gleaned from ransomware and data breaches is available on the dark web. Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data.
Buying or selling drugs, stolen credit card data, fake documents, or hacking services are all serious crimes. Exploring the Dark Web environment is critical for companies whose security depends on digital evidence. Criminals use these networks for illicit businesses, hacking services, and leakage of information. However, the Dark Web is not a bad place as it is also used by whistleblowers, journalists, and activists who cannot risk being exposed. ” from a business perspective, you will learn how anonymity can be used for both good and bad purposes.
While some dark web websites may contain such content as complex riddles or some eBooks, one thing will always remain; the dark web is for dark material. The best thing to do is get your hands on some good darknet directories to find secure pages regarding the stuff you want to search for. The dark web itself has a lot of dark web site directories to help you point out where you need to go. Setting up the Tor and VPN separately is recommended if this is a concern. If you want privacy and anonymity, NordVPN accepts payment in Bitcoin.
- The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment).
- Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online.
- All ISO publications and materials are protected by copyright and are subject to the user’s acceptance of ISO’s conditions of copyright.
- Google doesn’t index these sites, but other search engines do, including DuckDuckGo, and there are lists — including one run by Muffett — so you can find what you’re looking for.
You’ll need to find and navigate to the specific dark web addresses on your own. Content on the Dark Web exists on overlay networks that use the Internet and special tools and configurations to sustain security and privacy. Networks on the Dark Web mask sensitive information, like user locations, while conducting business by utilizing these complex systems. These networks are made of small Peer-to-peer (P2P) networks as well as larger networks like TOR. Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.



