We, therefore, use the following 4-step process to reduce the DWM dataset to a list of Bitcoin...
Uncategorized
For instance, you can choose the preferred security levels for enhanced protection. The security level is set...
Any online activity can carry breadcrumbs to your identity if someone digs far enough. When viewed through...
Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want...
In addition to tracking individual transactions, law enforcement agencies also focus on disrupting the infrastructure supporting illegal...
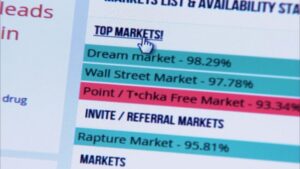
It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures....
They typically provide instant withdrawals and don’t require personal banking information for transactions. Purchasing Bitcoin comes next,...
Some marketplaces explicitly ban the trade of fentanyl, while others claim to prohibit it but fail to...
All of this has made it one of the most reliable markets still active in 2025. According...
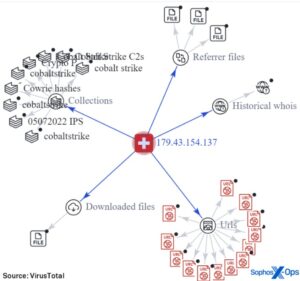
By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked...