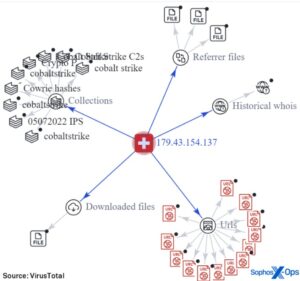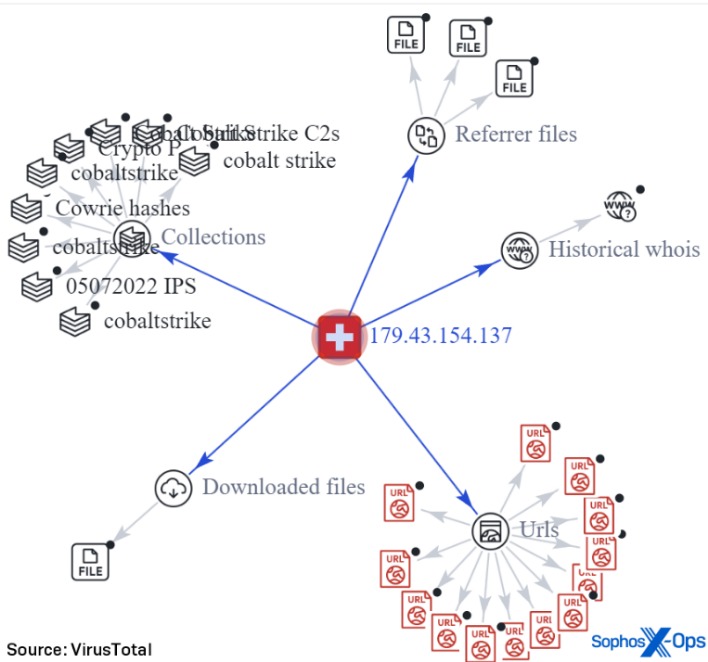
Fortunately, the forums offer an option for users to operate under pseudonyms that help protect their identities. It’s the best way that users can make open communications as well as share sensitive data without exposing themselves. XSS (formerly known as DaMaGeLaB) was one of the longest-serving forums in the deep web.
- So, even though it does exist on the internet, Google doesn’t index any of these pages or content.
- Criminal and antisocial behaviour appear to account for the majority of dark web activity.
- Other options include Ahmia and NotEvil, which focus on listing .onion links.
- Tor was designed to protect American intelligence communications online.
Alternative Networks: I2P And Freenet Overview
It routes users’ internet traffic through a network of volunteer-operated servers, known as Tor nodes, which helps protect users’ privacy by obscuring their IP addresses. The Onion Internet Protocol address (.onion) also replaces the actual IP address of the sender’s computer, meaning the physical location of the sender is also masked. Only the first and last nodes can reveal the identity of the sender and the content of the message. As conventional browsers cannot display .onion addresses without considerable modifications, Tor clients are also encouraged to use the Tor Browser, a version of Firefox.
Can I Access The Dark Web With The Tor Browser?
If we have made an error or published misleading information, we will correct or clarify the article. If you see inaccuracies in our content, please report the mistake via this form. The dark web is a double-edged sword, offering anonymity but also posing significant risks. It’s a hub for illicit activities, with cybercriminals ready to exploit any weakness. Without the right precautions, your IP address could be exposed, leaving you vulnerable to hacking, tracking, or even identity theft. However, this does not provide any extra security for your device or information.
The Best Dark Web Links — Safe & Verified Sites In 2025

Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship.
Can My ISP See That I Am Accessing The Dark Web?
Choose a VPN known for strong encryption, a no-logs policy, and compatibility with various devices. The “VPN-over-Tor” approach offers added protection, even if Tor is compromised. By encrypting communication before it gets to the Tor network, pairing Tor with a VPN gives a second degree of protection.
- Unlike the surface web, you can’t access deep web resources directly through a search engine; they require login credentials or special permissions.
- Alternatively, users can connect in opennet mode, which automatically assigns peers on the network.
- Tor, short for “The Onion Routing project,” is a free, open-source network built to protect online privacy and enable access to the dark web.
- The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe.
- We’re a nonprofit organization and rely on supporters like you to help us keep Tor robust and secure for millions of people worldwide.
But it also contains other news and religious sites, private discussion forums, and medical records. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo.
Step-by-Step Guide To Accessing The Dark Web Safely With Tor (
While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. Anyone concerned about user privacy, anonymity on the internet, and digital security should consider downloading the Tor Browser. It gives you a way to experience the internet in a more private and protected way, as it uses the Tor network to route your traffic. This connection method is based on multiple distributed nodes linked to computers worldwide, effectively hiding things like your IP address or geolocation. This browser is based on the Mozilla Firefox browser but uses a Tor network to allow you to browse the internet anonymously. It can help you bypass censorship or access location-restricted content.
While you can’t install the Tor browser from the official website, Chromebook users can configure it via a few simple Linux commands. When you see a suspicious link, especially one containing seemingly random characters and numbers that cannot be resolved using public DNS, steer clear. These links containing said random characters and numbers are hard to verify as legitimate or safe. You can start your journey to a safer online experience for $4.99/month for a yearly plan, which allows you to connect 10 devices simultaneously and with a 30-day money guarantee.
How Do Onion Routing And Tor Work?
And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure. However, VPN over Tor connections provide poor privacy, as Tor servers can collect your real IP address. Plus, very few VPNs support VPN over Tor connections — and the ones that do require you to perform an inconvenient manual setup. I personally think the Tor browser is only good for surfing dark web links, while VPNs have many more use cases — they’re great for streaming, torrenting, gaming, and bypassing censorship.
University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions.
When you download and install the Tor browser on your device, you need to click the “connect” button on the landing page. You can use the Tor browser on Linux, macOS, Windows, Android, and iOS, and below are the steps for downloading and installing on each operating platform. However, how can you use it if you don’t know how to install the Tor browser on your device? This article highlights the easiest ways to configure the Tor browser on any OS.
When using this method, Tor will encrypt your request, which will pass through your ISP unhindered. From there, it will go through a VPN server that conceals your IP and wipes geo-locations tags and other elements your Government or ISP might use to track the request. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web.

How Can I Increase Security While Using Tor?
This means you should never change the default settings in the Tor Browser. Open the Downloads folder on your Mac, and double-click the file you just downloaded. Simply visit the Tor Project website, then click on the “Download Tor Browser” button found in the upper right-hand corner or the center of the web page.
By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. The last node (exit node), through which Tor routes your traffic, is delicate. In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts.
A VPN and Tor should be used together and it is advisable to connect via a VPN to Tor, rather than vice versa, for the best protection possible. However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups. Illegal marketplaces are merely a small fraction of what’s actually there.