
To make the most of Ahmia, start by accessing it through the Tor browser for enhanced privacy. Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe. Because dark web sites can only be reached with a dark web browser like Tor browser, the best dark web sites, best onion sites, and best Tor websites are all one and the same. And because they aren’t searchable via Google or Bing, onion site lists are important roadmaps to help users find what they’re looking for on the dark web. Behind the easily available sites indexed by search tools such as Google lies the Invisible Web (also referred to as the Deep Web).
What’s The Difference Between Surface Web And Dark Web Search Engines?
Some directories, like clones of the Hidden Wiki, may contain outdated or malicious addresses. We recently explained the dangers of these clones in our guide on The Hidden Wiki in 2025 – Real Link or Dangerous Clone? If you rely on such lists without double-checking, you may end up on harmful sites. DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web.
Halo Security Enhances Platform With Custom Dashboards And Reports
Centralized indexing (e.g., Torch, Haystak) is vulnerable to takedowns or operator bias. By 2030, blockchain-based indexing could create tamper-proof, community-driven .onion catalogs, aligning with NotEvil’s non-profit model. To help users decide whether premium tiers are worth it, here’s a comparison of free vs. premium features across engines like Haystak (and NotEvil’s free-only model for context). In another test, I searched for I2P content (“I2P forum”), but results were sparse, and I switched to a dedicated I2P tool. OnionLand’s polish is a game-changer, but its risks require caution. In 2025, I tested OnionLand for a dark web news aggregator for a media trends piece.
Even if you have good intentions, it’s easy to stray off the beaten path in the dark web and stumble onto illegal sites and materials. If you really do choose to visit the dark web, and have legitimate and legal reasons for doing so, it’s advisable to follow these security tips. Please remember that it’s not illegal to enter the dark web, but you browse there at your own risk and it’s your responsibility to abide by the law.
How Do Dark Web Search Engines Work?
The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity. TorLinks serves as a backup or secondary directory site to the popular Hidden Wiki. It’s divided into commercial links (from crypto services to gambling sites) and non-commercial links (like social media). As always, use Tor Links with care, as it includes onion links to dubious or illegal activity. Onion sites are considered part of the deep web because search engines like Google and Bing can’t index them.
- With these guidelines, exploring the dark web can be done securely and confidently.
- A great alternative is Mail2Tor, which enables anonymous sending and receiving of messages via webmail or email clients.
- By 2029, engines may support DID-based access to gated .onion communities, streamlining research while preserving privacy.
- Use the Tor browser, avoid unfamiliar sites, and be cautious with downloads.
Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data.
Subscribe To The Blog Newsletter
Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. Install Norton VPN to encrypt your internet connection and help protect the data you share online. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely.
Directory Of Open Access Journals
Kilos is a powerful deep web search engine designed for users seeking comprehensive access to the invisible web. It stands out for its extensive index, which includes over 553,994 forum posts, 68,860 listings, 2,844 vendors, and 248,159 reviews. This makes it one of the best search engines for dark web exploration. Kilos allows you to search across six major dark web marketplaces, offering a broader scope than its predecessor, Grams.
AccuKnox Awarded Patent For Runtime Security Of Kernel Events
Haystak is not just a search engine; it’s a gateway to the hidden depths of the internet. As we continue to navigate an era of information overload, efficient search engines like Haystak are becoming indispensable. By providing a secure and private search experience, Haystak empowers users to explore the dark web with confidence and curiosity. Launched around 2007, The Hidden Wiki is a legendary entry point to the dark web, though not a traditional dark web search engine. It’s a community-maintained directory of .onion links, organized into categories like forums, marketplaces, privacy tools, and file-sharing services.
Considerations When Exploring The Dark Web
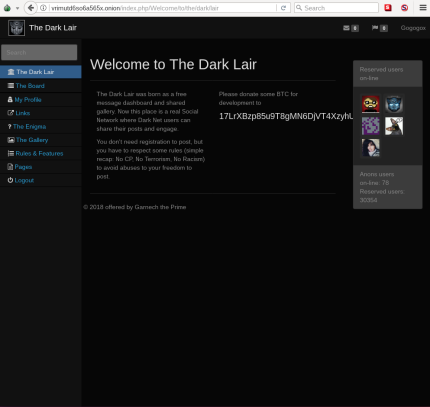
Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
Data Breaches And Scams
Renowned for its privacy-centric approach, DuckDuckGo has a version accessible via Tor, ensuring no logs of your searches are kept. Dark web engines like NotEvil index these domains exclusively, allowing keyword-based discovery of sites that surface engines can’t reach. They’re essential for secure access but require verification to avoid phishing mimics. These newcomers focus on user trust and cross-network support (e.g., I2P), but verify their .onion stability via communities. They complement established ones like NotEvil, offering fresh features for niche research.
- A VPN also helps you bypass geographic restrictions and protects you from potential cyberattacks.
- Even if you have good intentions, it’s easy to stray off the beaten path in the dark web and stumble onto illegal sites and materials.
- By using a dark web search engine and securing your connection with Forest VPN, you can explore safely and confidently.
- One of the best examples of a news source that is unavailable in some repressive nations is the BBC website.
- Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy.
These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted.


For safety, use a VPN first, enable device-level protections like app sandboxing, and avoid public Wi-Fi to prevent leaks. Mobile Tor is slower, so opt for lightweight engines like DeepSearch, but always verify .onion links and limit sessions to reduce battery drain and exposure risks. The dark web subset demands higher security due to potential illicit content, making specialized tools essential. Using dark web search engines is generally legal, as simply browsing or searching the Tor network isn’t prohibited in most countries—it’s the activities you engage in that matter.
While this filtering is intended to improve user safety, it can also prevent access to content that is relevant for research or dark web activity monitoring purposes. This search engine’s indexing is relatively shallow compared to other uncensored engines, meaning many dark web sites remain undiscovered or unlisted. Like traditional search engines, dark web search engines also use web crawlers, but not the same ones. The difference is that they are specialized web crawlers designed to operate within the Tor network and index .onion sites.
Use obfuscation tools like bridges, avoid patterns in searches, and layer with VPNs to reduce traceability, though nothing is 100% foolproof against sophisticated adversaries. Directories like Torlinks provide curated, categorized links for quick, structured access to trusted sites, pros including ease for beginners and reduced spam exposure. Cons are outdated entries and no keyword search, limiting discovery.



