With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader. Credit card hacking can take many forms, and it’s essential to understand the different types to protect yourself. Data breaches have become a fact of life, but taking proactive steps can help minimize the damage. Slim CD, the company responsible for the breach, has taken steps to implement additional safeguards to its network. Companies affected by the attack included Nasdaq, 7-Eleven, Carrefour, JC Penney, Hannaford, Wet Seal, Commidea, Dexia, JetBlue, Dow Jones, Euronet, Visa Jordan, Global Payment, Diners Singapore, and Ingenicard. Your lender or insurer may use a different FICO® Score than FICO® Score 8, or another type of credit score altogether.
India Data Breach: 460,000 Credit Card Details Put Up For Sale On Dark Web
These platforms provide a marketplace for payment card data stolen by a variety of actors, leading to further specialization in crime. Cybercriminals trade their illicitly acquired data on various dark web/hacking forums by advertising or leaking a sample of the data to lure other malicious actors in the community. Recently, adversaries illicitly obtained over three million customers’ credit card information after compromising Dickey’s BBQ Pit Point-of-Sale (POS) systems in 156 restaurant locations. Attackers posted the stolen data for sale on Joker’s Stash, a dark web marketplace that exclusively trades stolen card data. The hackers’ group advertised a massive collection of payment card details for sale, dubbed “BLAZINGSUN,” at $17 per card. There might be various cybercriminal activities operating online, but stealing users’ sensitive information and peddling it on darknet markets is the primary activity for most threat actors.
List Of Recent Data Breaches In 2025
In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research. Notably, cryptocurrency has become a valid option for carding operations, whether through exploiting stolen crypto wallets and accounts or using stolen credit card details to purchase cryptocurrency. These details often land there after data breaches, phishing attacks, or malware infections that steal information from unsuspecting users. If your credit card number appears on the dark web, it means someone has likely leaked or stolen it—and now it could be traded, sold, or used without you even knowing about it. Indeed, in the last six months of 2020 alone, threat actors offered more than 45 million compromised cards for sale in underground credit-card markets monitored by security firm Cybersixgill, the company said in a report.

Claimants needed to submit documentation by November 18, 2024 showing unauthorized access or financial loss between August 2018 and August 2024. Payments are being sent out by direct deposit or check and are expected to be completed before the end of 2025. An Israel-linked hacking group known as Predatory Sparrow (Gonjeshke Darande) claimed responsibility, stating it had “destroyed” bank data during the incident. Predatory Sparrow has previously conducted destructive operations against Iranian infrastructure. United Natural Foods Inc. (UNFI), the main distributor for Whole Foods and supplier of over 250,000 grocery products, confirmed a cyberattack in June 2025 that forced a full network shutdown. The incident, disclosed in its Q3 earnings report, continues to disrupt fulfillment and supply operations.
Dark Web credit cards can be a nightmare for victims, often leaving them with significant financial losses and damaged credit scores. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online. BidenCash shop was established in April 2022, following the seizure of other card shops and carding platforms by the Russian authorities. Since its inception, it has been attracting the attention of both old and new cybercriminal customers. This post will discuss deep and dark web credit card sites, specifically the top illicit credit card shops.
Credit Cards Skimmed And Used As Marketing Tool
Millions of customers’ card data have been compromised in the past decade. No matter how vigilant you are, there is nothing you can do to prevent a data breach on a merchant’s website, but using a virtual card can shield your actual card data from being exposed. Stolen credit cards are often used to make purchases at specific sites that don’t have protections against fraud. Full or partial credit card details are commonly sold on the dark web, including BIN numbers, credit card numbers, expiration dates, and CVV numbers. Deep and dark web credit card sites include forums and marketplaces that host the trade and share of illicit content relating to credit cards.

How To Spot And Avoid Personal Loan Scams
Scanning the dark web helps you detect if your credit card number has been exposed. Once exposed, your card details can be used for unauthorized transactions or fraud. Early detection lets you take immediate action to protect your finances, such as alerting your bank or requesting a new card to avoid further risks.

Formerly known as Hunters International, World Leaks appears to be dropping traditional ransomware tactics in favor of direct data leaks, bypassing encryption and ransom negotiations. The UK Ministry of Defence set up a covert Afghanistan Response Route (ARR) following the breach. The program has since resettled 4,500 people, with another 2,400 expected, at a cost of £850 million. A successful attack could severely impact confidentiality, integrity, and availability of Teams data. The issue was one of 107 vulnerabilities patched in August, which also included a fix for a Windows Kerberos zero-day.
Methodology And Prevention
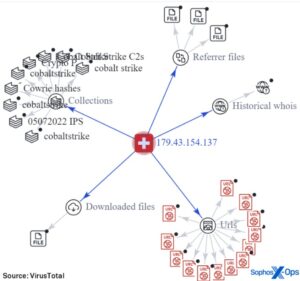
If the investigation reveals serious or repeated privacy breaches, the commissioner has the power to seek civil penalties through the Federal Court of up to $2.2 million per contravention. The agency will examine the personal information handling practices of Optus and its parent company. The cards affected are mostly VISA, Mastercard and American Express cards. However, we have also noticed that some search terms related to these topics appear to be shadow-banned by Telegram. Users now need an exact channel name or link to surface some of these channels, instead of being able to search key fraud-related terms and return all of the public channels with those terms in their names and descriptions. We actively monitor Telegram and were able to independently confirm what appears to be increased content moderation in the form of removing or deactivating channels used to discuss fraud and cybercrime.
Sending Phishing Links
This opens the door to applying for loans, creating fake IDs, or taking out credit cards in your name. It can take months—or even years—to recover from this kind of identity fraud. Recent studies reveal that 63% of U.S. credit card holders have been victims of fraud, and over 50% experienced it more than once. With data breaches happening more frequently, your credit card details could already be circulating on the dark web—without your knowledge.
- All information, including rates and fees, are accurate as of the date of publication and are updated as provided by our partners.
- Earlier this year, a New York man pled guilty to managing a credit card theft scheme responsible for stealing $1,500,000 from 4,000 account holders between 2015 and 2018.
- The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details.
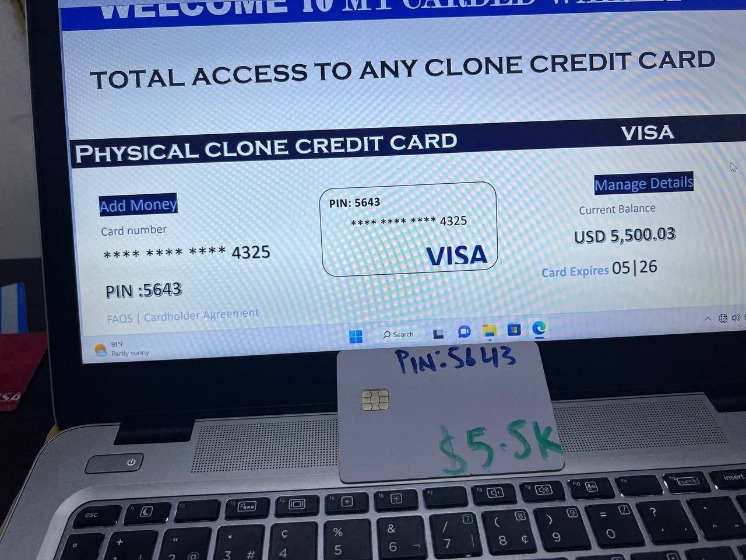
- Vendors sell additional information about the cardholder, known as “fullz”, which includes the cardholder’s social security number, street address, birth date, and more.
Vendors sell additional information about the cardholder, known as “fullz”, which includes the cardholder’s social security number, street address, birth date, and more. Although it offers leaks from many different countries, the site has a dedicated lookup and leak section for Canadian profiles, making it extremely easy to use for buyers interested in Canadian leaks. The site also has a unique news section, listing new leaks and their size. BidenCash is considered to be one of the most popular credit card sites today and serves as the official sponsor of the popular credit card site Crdpo. Information and Privacy Commissioner Angelene Falk urged all organisations to review their handling of personal information and data breach response plans.
- But while you can’t undo a data breach, you can take control of what happens next.
- Cass-Gottlieb told a parliamentary committee there had only been a few instances of fraudsters successfully scamming victims out of money by pretending to be from Optus.
- Adding fullz to a card purchase increases the price by about $30 for a physical card and under a dollar for digital card info.
- Renowned cryptocurrency trading platforms and wallets, such as LocalBitcoins, Kraken, and Coinbase, featured in dark web listings ranging from $90 to $250.
Reach Your Financial Goals

It’s important to detect fraud when a threat actor is trying to use stolen payment information to make a purchase from your business. Tools like an Address Verification Service (AVS) can help detect fraud in online purchases by comparing a customer’s billing address with the address on file with the issuing bank. Flare’s Dark Web Monitoring platform monitors dozens of .onion sites for credit card fraud, BINS and other financial fraud related data.
The disruptions extended to civilian services, with local reports indicating several wedding cancellations due to system outages. In October 2024, the Dutch National Police disclosed a data breach that exposed the names, email addresses, and phone numbers of nearly 63,000 officers and staff members. In November 2024, retail chains Hot Topic and its subsidiary BoxLunch suffered a data breach affecting nearly 57 million customer records.
CEO Sandy Douglas said UNFI is “safely bringing systems back online” and shipping to customers “on a limited basis.” The company’s external-facing systems—including supplier web portals and VPN tools—remain offline. The attack stemmed from a social engineering campaign where threat actors impersonated HR or IT staff, contacting employees by phone or text to trick them into granting access. The attackers gained entry to Workday’s third-party CRM platform, not its core systems. The attackers obtained approximately 2.55 million records containing basic business contact information such as company names, phone numbers, and related notes.