However, if the pen is applied to counterfeit money, it will leave a dark or black mark. The ink must possess the same color and consistency as the ink used in genuine banknotes. Additionally, counterfeiters may need to obtain specific ink formulations that replicate the security features found in authentic currency, such as color-shifting ink or ink that reacts to ultraviolet light. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web.
Caution: Safety Comes First When Visiting Dark Web Links
- Additionally, international cooperation among law enforcement agencies has proven to be instrumental in combating financial crimes on the dark web.
- It was registered to Ross Moore of Florida, a real person who had reported his identity had been stolen.
- We ensure that issuers throughout the world safeguard their banknotes for the Cash Cycle.
- And when it comes to paying, the site sticks to Bitcoin (BTC) and Monero (XMR) to keep transactions private.
- These interactions help law enforcement track the identities and operational tactics of criminal organizations.
Tor remains the most prevalent method due to its ease of use and robust anonymity features, but the popularity of I2P is steadily growing due to its increased resistance to surveillance and censorship. Furthermore, criminals may employ shell companies and offshore accounts to move money across borders and disguise its origins. These methods make it difficult for authorities to detect and prevent money laundering activities on the dark web, posing a significant challenge for law enforcement and financial institutions. If you think the Dark web marketplaces are just online shops, you’re wrong — these sites are the actual weapon stores for criminals. They provide criminals with access to everything they need, from launching attacks to stealing data, etc. The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities.

Fake Kuwaiti Dinar Banknotes
Law enforcement agencies around the world are working diligently to crack down on these operations. Advanced technologies such as machine learning and blockchain analytics are being used to trace suspicious transactions and identify the sources of counterfeit currency. Public awareness campaigns also play a crucial role in helping individuals recognize fake bills and avoid falling victim to scams. The successful takedown of Wall Street Market in 2019 involved simultaneous operations coordinated by law enforcement agencies in Germany, the Netherlands, and the United States.
Counterfeit Banknote Listings On Dark Web Spike By 91%
“The money really looked good. The feel of the bills was the giveaway,” Powell stated. “As far as marking them with the pen, they would mark true as a good one hundred dollar bill but the texture of the bill was different.” Investigators believe the men were also involved in other money schemes in other states. The driver and passenger were identified as the men caught on video at the Dollar General passing the fake money, the sheriff said. They were transported to the Crenshaw County Jail and the van was towed. Agents suspect it is a digital key to unlock a bitcoin or computer vault.

Nevada “Network Security Incident” Shuts Down State Offices And Services
Agents often infiltrate dark web marketplaces by posing as buyers or vendors to gather intelligence on illegal activities. Undercover agents create convincing fake profiles, interact with criminal vendors, and conduct controlled purchases. These interactions help law enforcement track the identities and operational tactics of criminal organizations. Given the anonymity and encryption inherent to the dark web, authorities have adapted by developing specialized investigative methods and cross-border cooperation. Additionally, criminals may use online gambling sites to launder their dirty money by placing bets and then cashing out, effectively legitimizing their illicit funds. Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services.

Criteria For Choosing The Best Dark-Web Marketplaces

The accessibility and perceived anonymity of the dark web make these transactions increasingly common, highlighting an escalating security challenge for law enforcement and government agencies worldwide. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses. In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere. You should be aware that law enforcement agencies may be monitoring the dark web and that visiting certain websites or engaging in illegal activities can result in criminal charges. You can also check out this ultimate dark web safety guide to browse safely.
Cutting And Assembling The Banknote
The indictment states that they began operating Empire Market on Feb. 1, 2018. An intuitive, user-friendly interface is crucial, especially given the complex nature of dark-web interactions. Users favor marketplaces with straightforward navigation, efficient search functions, and clear product categorizations. The ability to seamlessly communicate with vendors via secure messaging systems also greatly improves overall user experience. There was a double-digit increase in deep and dark web ads and sellers promoting counterfeit currency last year, hinting at rising demand from the criminal community, threat intelligence experts have warned.
Aldon indicated that the other man with him, Shahal Lewis, of Stone Mountain, was his friend who came along for the money. Lewis was already on state probation, investigators say, and had a warrant out of Maryland. One of the clerks was too scared to say anything while the men were still in the store. She waited until they left, and then notified her supervisor who called 911. The store’s staff members were able to give authorities a description of the vehicle the suspects were both riding in, a rental U-Haul van. On Aug. 9 around 5 p.m., two men went into the store and bought a few items.
- At All in one document, we use sophisticated equipment to produce quality counterfeit money for sale and ensure it is unlikely to be detected as not genuine.
- As the months passed, Johnson suffered frequent nightmares and spent time on strange conspiracy websites.
- Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
- Nemesis Market is a relatively new wallet-less shop on dark web where you don’t need to deposit any amount in your wallet before buying products from here.
- With his expertise in budgeting, investing, and money management, he shares practical advice and valuable insights to help readers make informed financial decisions and build a secure future.
Dark-web marketplaces attract sophisticated cybercriminals adept at launching phishing scams, malware attacks, or ransomware threats. Buyers and sellers frequently face risks from malicious actors posing as legitimate vendors or customers, potentially leading to financial loss or exposure of sensitive personal information. In fact, everything is in English, and the site picks up users everywhere in the world.
Microsoft To Make All Products Quantum Safe By 2033
UV and magnetic inks are two additional security features that counterfeiters try to replicate. UV inks are invisible to the naked eye but become visible under ultraviolet light. Magnetic inks, on the other hand, contain magnetic particles that can be detected by magnetic ink character recognition (MICR) devices. To simulate intaglio printing, counterfeiters use a process known as embossing. They create a raised design or pattern on a metal plate and then use this plate to press the design onto the paper during the printing process.
Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. In 2013, the FBI shut down the Silk Road, but it was later relaunched in 2014 with the new name of Silk Road 2.0, but the German authorities shut it down in the same year. Other than the Silk Road 2.0, similar marketplaces also emerged, but they all went down sooner or later.
If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions.
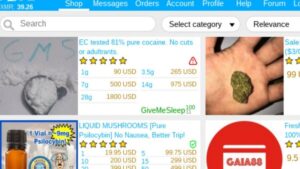
Listings for fake documents typically detail the quality of the forgery, the region or jurisdiction covered, price ranges, and turnaround times. Vendors often showcase sample images and customer reviews, reinforcing credibility and trust. At Dark Web Notes, we are the best and most unique producer of high-quality undetectable counterfeit money.

Explore techniques for designing, printing, and assembling counterfeit money while simulating security features and evading detection systems. Monitoring the activity on these platforms is crucial for fraud detection, brand protection, and financial intelligence. Because of the level of anonymity, these sites allow cybercriminals, it is critical to use powerful dark web monitoring tools, such as Webz.io’ Lunar, to track emerging financial and reputational threats. This is how the site admins encourage users to post their stolen credit card details on their site first. In addition to these types of listings, there are other free tools usually available on credit card sites. These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases.

This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously.