
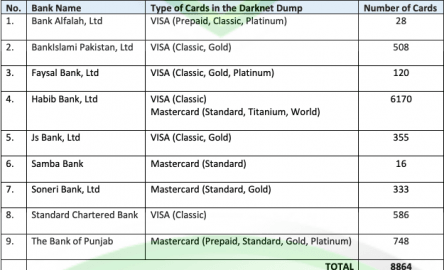
This data dump represented one of the largest breaches in history, with only the Equifax data breach (discussed below) eclipsing it in terms of scale. Companies that suffer from data breaches caused by credit card dumps face various costs, including remediation expenses, notification fees, legal liabilities, and reputational damage. In some cases, these expenses can run into millions of dollars and may lead to significant losses in revenue or even bankruptcy.
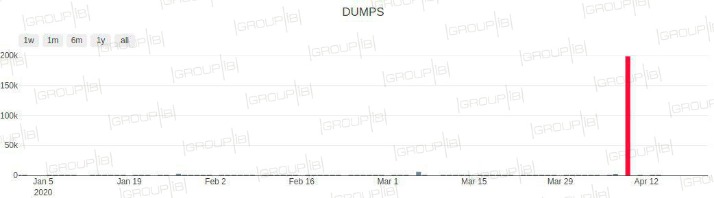
Together, we can work towards a future where digital transactions are secure, and individuals can make financial transactions with peace of mind. As reported by Bleeping Computer, in an effort to attract cybercriminals to its platform, the hackers behind ‘BidenCash’ have distributed the details of 1,221,551 credit cards. Crucially, she also outlines what service providers—including telcos, financial services, and insurers—can do to help protect consumers from carding in today’s shifting cyber threat landscape. This category, known as Dumps on the dark web, encompasses the raw magnetic strip data of credit cards.
OUR PLATFORMS AND BRANDS
Checkers are tools used by individuals and organizations to verify the validity and authenticity of credit card information and are used by threat actors to check the illicit information they purchase. The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details. Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. Thank you for joining us on this exploration of credit card transactions on the Dark Web.
- Changelly makes it easy to buy Bitcoin instantly with a credit or debit card.
- Dark web credit card numbers are stolen card details sold on hidden websites.
- Dark web monitoring platforms, such as Lunar, provide an automated solution to safeguard personal identifiable information (PII) and credit card details.
- You can also buy followers, with 50,000 Instagram followers costing would-be influencers US$250.
- To ensure larger reach, the crooks distribute the collection via a clearnet domain and on other hacking and carding forums.
- WeTheNorth is a Canadian market established in 2021 that also serves international users.
What Should I Do If My Card Is Stolen?
Cyble researchers noted that threat actors claimed that 27 percent, according to a random sampling of 98 cards, are still active and can be used for illegal purchasing. Leaking credit card credentials has become a very common phenomenon on chat applications, particularly Telegram. In fact, the overwhelming majority of leaked credit cards in past months originate from Telegram channels. Carding groups and channels reach up to tens of thousands of members, as they are easy to navigate and readily accessible. This stolen information is exploited by threat actors for financial gain through unauthorized charges, account takeover, and identity theft.
Legal Consequences Of Fraud
Skimming devices have been reported to be used at gas stations, restaurants, and other high-transaction locations. Companies such as my #1 pick, Identity Guard, can monitor your Social Security number (SSN) and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals. These criminals released the details of 740,858 credit cards, 811,676 debit cards, and 293 charge cards.
How Dumps Credit Cards Work
- Russian Market has consistently remained one of the most popular and valuable data stores on the dark web.
- While it shares a similar purpose with Joker’s Stash, there is no confirmed connection between the two.
- In the relentless battle against cyber threats, financial institutions must deploy proactive strategies and technologies to mitigate risks and protect customers, especially in the context of compromised credit card feeds.
- Dark web credit card fraud poses serious risks to consumers and businesses alike.
- Unauthorized use of credit cards affects about 10 million Americans every year.
- Breachsense monitors the dark web, Telegram channels, hacker forums, and paste sites for external threats to your organization.
Hacking involves the criminal gaining unauthorized access to a company’s computer systems that store credit card data. In large-scale attacks, hackers can steal millions of records at once by exploiting vulnerabilities in payment processing networks or third-party service providers. The largest known credit card dump to date occurred in 2017 when Equifax reported the theft of over 143 million records. Organized criminal groups have recognized the potential profitability of credit card dumps and have turned it into a lucrative business model. These groups invest in advanced tools, techniques, and infrastructure to target victims and monetize their stolen data. They sell the information in various forms, such as individual card numbers, cardholder details, or entire databases, depending on the demand and price range.
What Is Carding In Cyber Crime?
Thieves often buy cards to use on specific sites that don’t have security features like Verified by Visa (VBV) or MasterCard’s SecureCode. These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs. From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid. The “special event” offer was first spotted Friday by Italian security researchers at D3Lab, who monitors carding sites on the dark web. CVV Union is a basic card shop that is ideal if you are looking for specifc card attributes. It features an extensive interface to the database which you can query with a lot of different parameters.
Indicators Of Theft Of Credit Card Information
Considering this backdrop, it is evident that b1ack’s primary goal has consistently been to profit from the sale or use of these stolen credit card details. By leveraging dark web markets, underground forums, and direct transactions, they aim to capitalize on the extensive reputation and reach they have established through their effective marketing strategy. The Dark Web is an anonymous part of the internet accessible only through specific browsers and networks. It hosts a variety of illicit activities, including drug trafficking, weapons sales, and credit card dumps. Criminals sell stolen credit card information in different formats, such as CVV codes (Card Verification Value), full cards, or complete dumps of thousands to millions of records. One critical action a company must take when facing a credit card dump is to notify customers of the breach as soon as possible.
Can I Buy Bitcoin With PayPal, Google Pay Or Apple Pay?
Card data is a hot commodity on the dark web, with credit card details and cloned cards being sold to cybercriminals. These stolen cards can be used for financial gain through unauthorized charges, account takeover, and identity theft. In a more recent development, on February 19, 2025, B1ack’s Stash escalated its operations by claiming to leak an additional 4 million stolen credit card details for free. This massive data dump was publicized on underground cybercriminal forums like XSS and Exploit, serving both as a marketing tactic and a means to establish credibility within the cybercrime community.
Criminal charges such as identity theft, fraud, or computer crimes can result in imprisonment, fines, probation, or a combination of these penalties. Card theft, scams, and black markets for personal IDs have been around since the advent of credit cards in the 1960s and ’70s. To prevent dumps credit cards, individuals should be cautious when providing credit card information online or in public. Dumps credit cards can lead to significant financial losses for individuals and businesses.
In 2020, customers apparently complained about the “decline in quality” of the site’s stolen data, with concerns raised regarding the validity of the posted information. The site’s operator also apparently contracted covid-19, according to a post on the site’s forum in October. AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble. “Our analysis suggests that this market has been around since May 2021 and is available on a Tor channel as well,” according to the post.
The consequences of a credit card dump can be severe for both consumers and companies. Consumers face financial loss, identity theft, and potential long-term damage to their credit scores. Companies can experience significant reputational damage, regulatory fines, and financial losses due to potential lawsuits and customer compensation.

Shuttered Dark Web Marketplaces
As consumers increasingly rely on credit and debit cards, the risk of having your financial data stolen is a growing concern. Here are some best practices that can help reduce your risk of becoming a victim of a credit card dump. Cybercriminals resell the credit card information on the black market or use it themselves to make unauthorized online purchases using stolen credit cards.
Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web. It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures. Its focus on financial fraud and high-value transactions has attracted a dedicated user base, contributing to its growing reputation and market value. But the darkness of these deals doesn’t perfectly hide criminals from accountability.
It includes critical information such as the bank account number, account balance, service code, PIN code, and card verification code. These details are primarily sought for physical use, enabling activities such as cash withdrawals from ATMs. Once the criminals have obtained this data, they create a credit card dump.



