
With carding becoming a bigger threat than ever, it’s wise to learn more about it and take protective measures. Read along to find out how it works, red flags to watch for, and tips for keeping yourself safe. Chinesecybercriminals have become highly active in defrauding consumersworldwide by exploiting NFC technology and leveraging specializedtools to abuse NFC-enabled point-of-sale (POS) terminals. Theirtactics involve sophisticated schemes, such as relaying stolen NFCcard data, registering fraudulent POS terminals by money mules, andconducting large-scale unauthorized transactions. These criminalsexploit the convenience and widespread adoption of NFC technology,targeting vulnerabilities in payment systems and taking advantage ofpoor security measures.

While much attention is often focused on the perpetrators and their illicit activities, it is crucial to shed light on the victims who bear the brunt of these crimes. The human cost of carding and credit muling cannot be understated, as innocent individuals and businesses suffer severe financial and emotional consequences. In this section, we will delve into the various ways in which victims are affected by these illegal practices, offering insights from different perspectives and exploring potential solutions.
Hacking Forums In 2023
The more high-profile the work, the fewer details employers may want to give away due to operational security concerns. In most cases, the larger, more sensitive, and technically difficult the project, the more likely the commissioning buyer would want the developer to be working within a team. That way, they can more closely oversee the project and ensure it’s coming along on time and to spec. Projects like these likely involve large botnets, banking trojans, and sophisticated ransomware.
Use Monitoring Tools – Avoid Accessing The Dark Web Yourself
NFC-related fraud is on the rise, as evidenced by cyber threat intelligence analysts at Resecurity. Numerous banks, FinTechs, and credit unions have reported increased NFC-related fraud and highlighted significant challenges in early detection. Chinese cybercriminals demonstrate high adaptability in exploiting NFC technologies for fraudulent purposes and create new tools to facilitate illegal operations at scale. They target financial institutions to defraud consumers and cause substantial economic losses for the global economy.

ReliaQuest Internship Program Prepares Students For The Future Of Cybersecurity
Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. Russian Market has consistently remained one of the most popular and valuable data stores on the dark web. The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy.
What Happens On Dark Web Forums?
Carders utilize a wide array of tools and techniques to maximize their success rates. These include carding forums, where they exchange information, tutorials, and tips with fellow criminals. Carders also rely on sophisticated software and malware to exploit vulnerabilities in payment systems. Some even employ techniques like “phishing kits” to trick unsuspecting individuals into revealing their card details.
How Carding Impacts Businesses And Customers
Dread is a dark web forum designed to mimic the structure and functionality of Reddit, featuring a familiar and user-friendly interface for its members. Dread has rapidly become one of the most significant platforms for discussions related to illicit activities, including hacking and cybercrime. Its popularity surged after Reddit banned several darknet market discussion communities, leading many users to migrate to this platform.
How Businesses Can Protect Themselves Against Carding
Transactions on dark web forums typically use cryptocurrencies like Bitcoin and Monero. These digital currencies offer anonymity and are difficult to trace, making them ideal for illegal transactions. Ransomware-as-a-Service (RaaS) groups, for instance, use these platforms to find affiliates and partners. These services act as intermediaries, holding funds until both parties fulfill their obligations. In addition to a clearnet domain, they also shared the new URLs through various hacking and carding forums.
- When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks.
- Carding is a type of payment fraud that involves testing stolen credit card information on merchant websites to verify if the details are still valid.
- It provides them with valuable information needed to carry out a variety of attacks.
- Cybersecurity experts should pay close attention to these trends, as they often indicate emerging threats and profit-generating tactics among the cybercriminal forums.
- At the heart of every carding forum lies the administrator, the puppet master orchestrating the illicit operations within the community.
- As one of the most active forums on the dark web, Cracked.io attracts cybercriminals, hackers, and individuals interested in exploiting various digital vulnerabilities.
BidenCash Dark‑Web Marketplace Takedown (June
Reputable actors active on this forum are often very sophisticated, acquiring a portfolio of positive reviews over the years. Although discussions about ransomware are banned, multiple ransomware-as-a-service (RaaS) operators are still active on the forum to purchase initial accesses or coordinate with partners. The forum is used for all cybercriminal types, but a particularly large population of initial access brokers have been observed, especially in the “Auctions” section of the forum. The ongoing evolution of cybercrime underscores the importance of constant vigilance, adaptability, and proactive investment in emerging security technologies and practices. Staying ahead of carding threats will depend heavily on innovation, cooperation, and a clear-eyed understanding of evolving criminal methods.
- Even so, we don’t consider the “death of carding”—which so many threat actors fear—imminent.
- These stolen cards have value because they can be used to purchase expensive items or gift cards, which can then be resold for cash.
- You can check out privacy-focused payment methods like PayPal, Apple Pay, Google Pay, or even prepaid cards.
- These bots automate the process of making small transactions on e-commerce websites to test if the card is active, and they can be used without triggering fraud alerts.
Although the anonymous administrator behind the marketplace was never publicly identified or arrested, authorities seized multiple servers and cryptocurrency wallets, significantly disrupting global carding networks. As described previously, the initial stage involves purchasing stolen credit card details from dark-web marketplaces. Buyers—often called “carders”—carefully select cards based on criteria such as credit limits, cardholder locations, and issuing banks to maximize potential financial returns. Cybercriminals frequently target online retailers and business databases to directly access large amounts of stored credit card data. Hackers exploit vulnerabilities in software, website plugins, or weak cybersecurity measures.
While authorities have failed to shut it down, the forum hasn’t, fortunately, witnessed easy sailing either. For instance, in January this year, it was the target of Operation Talent, the law enforcement initiative that was coordinated by the FBI and international agencies. It’s an operation that led to Cracked losing the original domain, but didn’t disappear – it simply moved to the new address. Like BFH and some other forums listed in this article, Cracked also operates right on the surface web, then you don’t have to look any further. Cracked is arguably the most accessible forum when compared to other dark web counterparts.

Fraudsters or bots who are attempting credit card fraud need to make multiple attempts, and cannot change their device every time. They will need to switch browsers, clear their cache, use private or incognito mode, use virtual machines or device emulators, or use advanced fraud tools like FraudFox or MultiLogin. Forums can serve as platforms for these individuals to coordinate activities, share information, and launch politically motivated attacks. Escrow services ensure secure transactions, while feedback systems allow users to rate and review sellers, promoting reliability. These tools enable them to conduct attacks on individuals, businesses, and institutions.
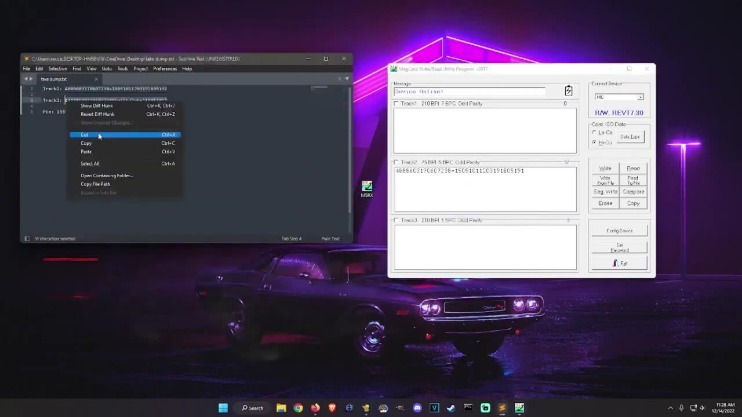
After it relaunched in June 2022, BidenCash initiated a promotional campaign that included sharing a dump of 8 million lines of compromised data for sale, which included thousands of stolen credit cards. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address.



