
We, therefore, use the following 4-step process to reduce the DWM dataset to a list of Bitcoin addresses where a “mining fee” can be deposited as intended by the owner of a BG site. Figure 3 presents a screenshot depicting the status of three cloned “Swedish Bitcoin Multiplier” sites as of November 20, 2024. The first site has been running on a rented server since January 29, 2024 (as shown in the “Discovered at” column).
Accessing blocked content can result in being placed on a watch list or imprisonment. The use of the dark web raises suspicion as it shows there is something you want to do privately. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom.

Dark Web Bitcoin Mining: Hidden Exploitation?
The site was used to launderhundreds of millions of dollars from these unlawful transactions. All told,the site had generated sales totaling more than 9.5 million in Bitcoinvalued, at the time, at approximately $1.2 billion. AlphaBay and Hansamarket, two of the biggest successors of Silk Road, were shut down in 2017.
- The dark web is a breeding ground for various crimes involving cryptocurrency.
- Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.
- The attackers provided step-by-step instructions on how to obtain Bitcoin and transfer the specified amount to a unique Bitcoin address.
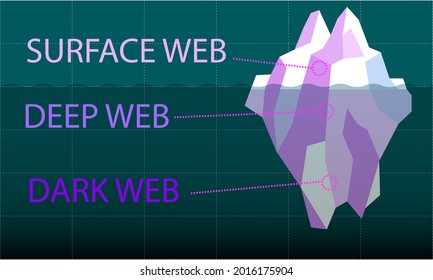
- You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here.
- It is a network where users can remain anonymous and engage in various activities, including the exchange of cryptocurrencies.
Mind Vs Machine: Are Engineers Trading Creativity For AI Convenience?
To access the Dark Web, you cannot simply type a URL into a standard browser. Instead, users must use specialized browsers designed to provide a high level of anonymity. In this article, we’ll explore the history of the Silk Road, its impact on the internet and cybercrime, and the legacy it left behind as the online marketplace that reshaped the digital black market landscape. The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider.
Eric Trump Praises China’s Role In Bitcoin, Says US And Beijing Are ‘Leading The Way’
However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome.

Onion Links: How To Access Them
The absolute most punctual excavators had the option to mine many BTC using only their Home Computers. To mine in the present BTC scene, you’ll need top-level hardware, which can slow down you two or three thousand bucks. Likewise, since Bitcoin has become famous now, you’ll have a ton of rivalry. You will find many more dark web wallets and also bitcoin mixers on the clear web, but most should be avoided since they are unproven and might not make your bitcoin anonymous. But which methods make your bitcoins really anonymous is hard to tell for most dark web newbies.

Anonymity And Privacy
Dark web monitoring tools automatically allow law enforcement agencies to view illicit marketplaces, forums, and communication platforms for signs of illegal activity involving cryptocurrency. By automating much of the intelligence-gathering process, these tools reduce the need for manual oversight and allow law enforcement to identify key trends, wallets, and services linked to criminal activity. This not only saves time but also provides law enforcement with actionable intelligence, even if they lack specialized personnel or resources to conduct deep blockchain analysis on their own. Dark web marketplaces have been a significant outlet for illicit trade, serving millions of users worldwide for over a decade. First, we propose an algorithm that categorizes users either as buyers or sellers, and show that a large fraction of the trading volume is concentrated in a small group of elite market participants. We find that the dominance of markets is reflected in trading properties of buyers and sellers.
Traditional financial institutions are not involved in bitcoin transactions, making it harder for law enforcement agencies to trace the flow of funds. Moreover, mixing services and tumblers further obfuscate the transactions, making it challenging to identify the parties involved. Bitcoin, being the most widely used cryptocurrency, is frequently involved in these crimes.
H Is Available For Trading!
Security patches often close vulnerabilities that hackers exploit.Consider using a virtual private network (VPN). A VPN encrypts your internet connection, enhancing digital privacy while browsing suspicious sites.Monitor your accounts for unusual activity diligently. Quick action can minimize damage if you spot anything amiss.Educate yourself about common scams in the cryptocurrency space. Knowledge is power when navigating these risky waters.Keep backups of essential data offline to ensure it remains safe even if online threats arise.
Cryptocurrency exchanges are online platforms where individuals can buy, sell, and trade various cryptocurrencies. These exchanges provide the necessary infrastructure for converting digital currencies into fiat currencies and vice versa. Law enforcement agencies have made strides in tracking down and prosecuting individuals involved in illegal activities on the dark web. However, the dynamic nature of the digital currency landscape and the constant evolution of anonymizing technologies pose ongoing challenges.
Updated Search Terms From Badawi Et Al
Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. For example, it maintains your privacy and enables you to access untraceable content and services. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved.

We dove into the 2021 report, which was published in February, to figure out how much truth there was in the notion that crypto is only being used by criminals. And while these are critically important types of crime to pay attention to, we are going to zoom in specifically on dark web marketplaces. On one hand, increased regulation and scrutiny may deter individuals from engaging in illegal activities, ultimately making the dark web a safer place. On the other hand, it may drive criminals to explore alternative options that offer better privacy and security. This could lead to the emergence of a new underground economy built around these privacy-focused cryptocurrencies.
We classify all entities either as sellers or buyers as a function of time. The result is a time series of lists of sellers and buyers for each period and for each market and the U2U network. The classification is performed in five steps (see Fig. 1), as detailed next.

A project proposal has been sent to the home ministry for the modernisation of the Department of Narcotics Control, including an increase in technological capacity. Mules were at higher risk of being caught because they frequented bank branches with video security camera. By analyzing smart contracts and public wallet addresses, investigators can gain insights into how assets are moved around the blockchain. Unusual transaction volumes, rapid movement between wallets, and activity on high-risk platforms can all be indicators of illicit activity. Many trading platforms and payment methods on the dark web that involve cryptocurrency are often fraudulent.



