Some have implemented distributed hosting, robust compartmentalization, and enhanced privacy features to mitigate centralized points of failure. The darknet market landscape has evolved through several distinct generations, each adapting to increased scrutiny, technological developments, and lessons from predecessor failures. Due to law enforcement, many markets now require invites, referrals, or verified PGP identities. “Markets have sort of varying levels of sensitivity to fentanyl-related sales,” he said. “Some claim they don’t do it, then don’t police vendors; some claim they don’t do it, but then they do. Some will be selling precursor products but not finished products.” “After major exchanges delisted XMR, we observed a significant increase in bitcoin inflows,” Jardine said in an interview with CoinDesk.
Upon entry, you will be guided to the market by a member of the building staff located at the entrance. The celebrate Black History Month, Philadelphia Union will be hosting a small business pop-up market that will take place every Thursday at the Union Power Plant in Chester. Although both Tor and I2P are anonymity networks, there are some key differences. The Tor market has its roots in the early days of the internet, when users were experimenting with new ways to communicate and share information anonymously.
- Vendors operate with lower overhead, passing savings to consumers while maintaining higher purity standards.
- After a major external shock in 2017, the S2S network shrinks but, unlike the multiseller network, recovers, and grows again (though slower than the multibuyer network).
- Every investment and trading move involves risk; this is especially true for cryptocurrencies given their volatility.
- The evolution of the ecosystem of all buyers and sellers obtained from the considered markets and the U2U network is shown in Fig.
Network Structure Of Transactions
- To prevent the users from DDoS attacks, it provides personal marketplace domains to high-volume buyers and sellers.
- Then, between 2017 and 2018, there is a drastic structural change in the multiseller network structure due to operation Bayonet, after which the connections almost vanished.
- Therefore, we analyse the temporal network where nodes are the active markets and an edge between the nodes represents the number of multibuyers between them, what we henceforth call the multibuyer network.
- The celebrate Black History Month, Philadelphia Union will be hosting a small business pop-up market that will take place every Thursday at the Union Power Plant in Chester.
- It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses. These markets are dangerous anyway and shouldn’t be accessed even if they’ve onion addresses. Just as there are new entrants, the dark web has its veteran markets too, and Brian’s Club is one such market. It has been in operation for more than a decade since its debut in 2014.
Dangerous Fake Or Malicious Vendors
From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet. These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services. In this article, you’ll find detailed overviews of the top ten Dark-Web marketplaces currently dominating the hidden internet landscape in 2025.
How Do Tor Markets Ensure Privacy?
We’ll explore their unique features, common use-cases—both legitimate and illicit—and the significant risks users face when interacting with these platforms. Using trusted directories, PGP encryption, and secure wallets helps protect against fraud. Finding verified dark web marketplaces is not as simple as searching on Google. Since these markets operate on the Tor network, they require .onion links that are not indexed by regular search engines. Darknet marketplaces emerged around 2011, with Silk Road setting the standard for how these platforms operate. Built on Tor, these sites mask IP addresses by routing traffic through encrypted relays, ensuring anonymity for both buyers and sellers.
The internet is a wide landscape that comprises the surface part – the internet that we all know and the hidden portion. The hidden part of the internet is the larger portion that features over 95% of the entire internet. This is the part of the internet known as the dark web, and it’s accessible via mainstream search engines such as Google. Using TAILS is yet another security measure that protects your online identity on the dark web.
Tracking Virtual Currency Transactions To Disrupt DNMs
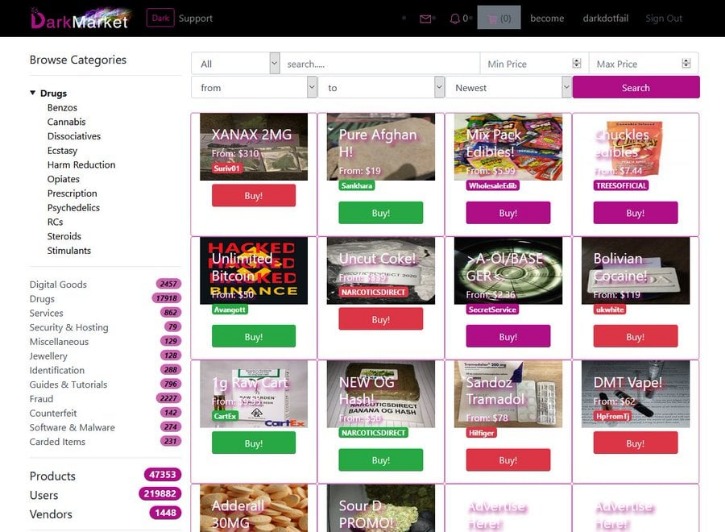
Some dark web listings claim to offer services like hacking-for-hire or even hitmen. DarkFail has been a darknet user’s companion since 2017, providing thoroughly vetted information on the best darknet markets, products, vendors, and security practices. Dark web markets are hidden online platforms in Tor where users anonymously buy and sell goods and services.
Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer. Monero is also popular among cryptojackers who hack into computers and steal other peoples’ power supplies to mine their own cryptocurrencies. Radar Rundown Hiding your IP address is one of the best ways to protect your online activities from … Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr… The unique part is that the platform offers free samples of stolen information, often to attract more customers.
How To Avoid Phishing Scams And Malware Threats
The sad reality is the fact that law enforcement agencies can’t track and prosecute perpetrators or even take down such content given the anonymous nature of the dark web. As much as authorities work hard to shut down various sites, it shows what the dark web is capable of doing if left unchecked. Discover everything about what is a darknet market, how it works, security threats related to it, and learn how to protect your data online. Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware.
How Do We Review Darknet Markets? 🔎
Create an account with a username, password, and email and complete the captcha. If you already own bitcoin, or have obtained some using one of the methods described above, you can skip this section. Otherwise, here’s how to purchase your first BTC on Localcryptos.com.
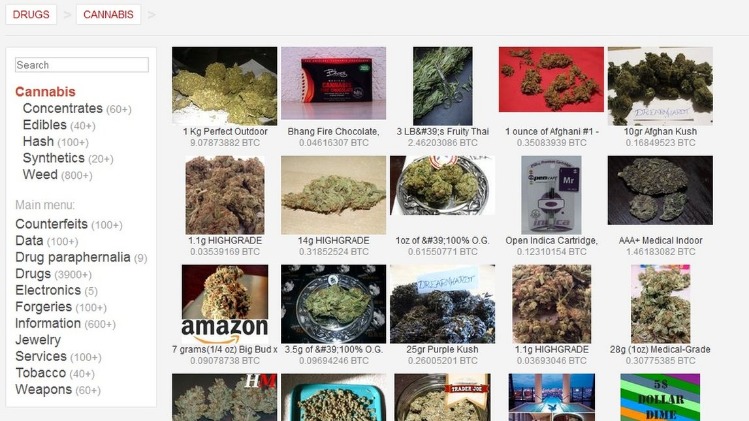
What You Can Buy On The Darknet Markets
Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals.
Nevertheless, due to their unregulated nature, DWMs exhibit behaviours not observed in regulated marketplaces. They offer anonymity to their users by using and developing specialized tools. DWMs are accessed through darknet browsers supporting the onion routing protocol (e.g., Tor), which provides anonymous communication connections35. Additionally, transactions are made with cryptocurrencies, mostly Bitcoin, which also provide anonymity to the transaction parties6,36. While the Bitcoin blockchain is publicly available on Bitcoin core37 or other third-party APIs such as Blockchain.com38, a market or a user can generate a new address for each transaction.
Later, in 2013, Silk Road caught the attention of law enforcement and policymakers like US Senator Charles Schumer, who publicly called for a federal crackdown. That push led to the arrest of Ross Ulbricht, the founder of Silk Road, after a long and intense investigation. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations. Current markets increasingly incorporate decentralization features, privacy-focused cryptocurrencies like Monero, and specialized focuses.
This use of cryptocurrency makes transactions fast and secure, and it supports the overall goal of privacy on the dark web. At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet. Our solutions empower you to monitor illicit darknet marketplaces and track emerging threats, ensuring you can take proactive measures to protect your organization and reputation. The darknet is a mysterious and often misunderstood part of the internet, attracting both intrigue and concern.

The nature of the dark web (anonymity and privacy) opens opportunities for drug dealers to reach a wide customer base across the globe without getting caught. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacyRadar.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. KEY TAKEAWAYS Whether you are using Android or iPhone, you can easily access the dark web on your ph… KEY TAKEAWAYS The Deep and the Dark web are the hidden part of the internet. Since the dark web can be accessed through the Tor browser, use a VPN with the Tor browser to ensure increased protection.



