Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web. As a result, you can be exposed to different malware types, including botnets, ransomware, keyloggers, and phishing.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
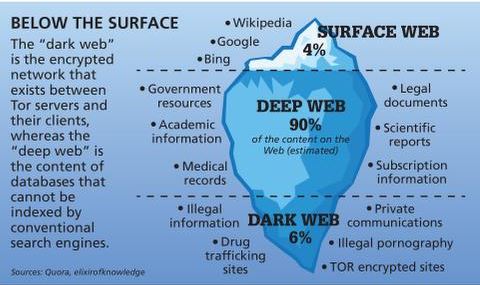
Most internet users access the deep web several times a day to perform common tasks, such as checking email, accessing a bank account, or reviewing health or school records. The deep web constitutes over 90% of online content and is inaccessible via search engines. It’s the portion that can be easily accessed by search engines like Google, Bing or Yahoo, and it includes websites that are publicly available to anyone with an internet connection. This includes most news sites, blogs, social media platforms, e-commerce sites and any other web page that doesn’t require special permissions or tools to view. The dark web is a small section of the internet intentionally hidden from traditional search engines and accessible only with special tools, such as the Tor browser.
Connect To A VPN Server And Launch The Tor Browser
Even if they aren’t actively malicious, they might still have weak security or expose you to threats. Additionally, make sure that you only download the Tor Browser from the official website. ExpressVPN is my top choice because it supports Tor traffic on all of its servers and works automatically without needing any additional configurations.
Unraveling The Truth About The NIST’s New Password Guidelines
Law enforcement officials can exploit that weakness using “Tor-exit-node” monitoring techniques to expose users’ IP addresses and potentially trace activity back to the original users. If you’re on the dark web to engage in illegal activity and your traffic passes through a compromised exit node, your secrets can be exposed. One study found that only 6.7% of Tor anonymity network daily users — a cohort that comprises mostly dark web users — connect to onion sites used for illicit activity. This essentially means that over 93% of Tor daily users use the dark web for legitimate reasons. Dark web encryption allows website owners and users to stay completely anonymous during their engagement.
End User Protection Against Exploitation By The Dark Web
- Understanding the differences and capabilities of various anonymity tools will help you make informed decisions about which networks best serve your needs.
- Dark web domains tend to be inconsistent — new ones pop up and others disappear, which makes sense if they offer questionable or illegal goods and services.
- The nearest server will typically provide the fastest and most stable connection speeds.
- However, it’s important to understand that no system or practice can offer absolute security.
- SecureDrop is a dark web link that allows whistleblowers on the dark web to communicate and share information with journalists safely and without being tracked.
- RiseUp is a top dark web website that offers secure email services and a chat option.
While such stories can cast the dark web in a negative light, it’s worth noting that there are numerous legal and beneficial activities accessible through it. I advise sticking to well-known, reliable sites and taking extra precautions to ensure your security. To avoid encountering disturbing or illegal situations, I advise against entering darknet sites before thoroughly researching them.
Limit Tracking On The Tor Browser
It also provides super-fast speeds, and its no-logs policy has been independently audited and confirmed — this way, you know it doesn’t store any user data. Plus, it backs all first-time purchases with a 30-day money-back guarantee, so you can try it out risk-free. There are several ways to protect your online activities from being tracked. Using a VPN is perhaps the easiest and most efficient way to protect your online travels from prying eyes, as it hides your real IP address, and encrypts all of your online traffic.
What Is The Dark Web? How To Access It Safely?
Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information.
While many dark marketplaces have been shut down by authorities, new ones soon appear in their place. The deep web is made up of content that search engines such as Google do not index. Such data includes medical records, financial information, research papers, private forums and networks, and other content.
The One-click Linux App I Use For Instant Online Anonymity
By leveraging these resources and staying connected with professional communities, you can keep abreast of evolving technologies, threats, and best practices. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. While the Dark Web remains a core venue for privacy-seeking users and covert activities, a range of emerging platforms and shifting trends shape the broader ecosystem of underground communication. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node.
If you manage to not expose your private information and avoid illicit activities, you can be sure everything will be okay. No one can force you to visit a drug-selling site, give out your info, and buy cocaine or something else. As long as you pick your sites carefully and use a safe and secure VPN, you’ll remain untouched and be able to browse this internet space indefinitely. PIA is popular in the USA because it offers servers in all 51 states. People in the United States and abroad can use it to venture into the dark web in privacy.
Keeping your security software up-to-date is vital in protecting your device from threats. Regular updates ensure your antivirus and firewall can detect and block the latest malware. It also adds an extra layer of anonymity, which is particularly important when browsing the dark web. Choose a reputable VPN service with strong encryption and a no-logs policy to ensure maximum privacy.

Simply put, accessing and browsing the dark web is perfectly legal. For example, it maintains your privacy and enables you to access untraceable content and services. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The anonymity provided by onion routing comes at the cost of slowing your internet considerably.
It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. When the dark web is mentioned online, it is usually in tandem with criminal marketplaces and arrests made by law enforcement agencies. The dark web, however, requires special software to access, as explained below.
How To Get On The Dark Web In 2025: A Step-by-Step Guide
Removing your sensitive personal information from the dark web once it has been exposed is virtually impossible. This irreversible process highlights the importance of taking preventive measures by utilizing a service that monitors your data for potential breaches. The encrypted data, such as WhatsApp messages, are secured behind end-to-end encryption and are not visible to your ISP. Tor Bridges or a VPN will help you to use Tor privately, as your ISP (Internet Service Provider) will not see that you’re connected to a Tor node. DarkWeb “marketplaces” guarantee confidentiality and anti-surveillance for your online purchases that you simply won’t find on any other websites. People who live under a government that deeply supervises or censors internet traffic eventually get attracted to the dark web.



