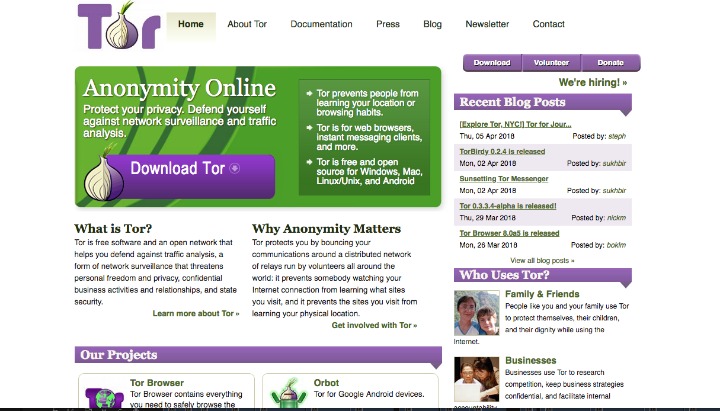
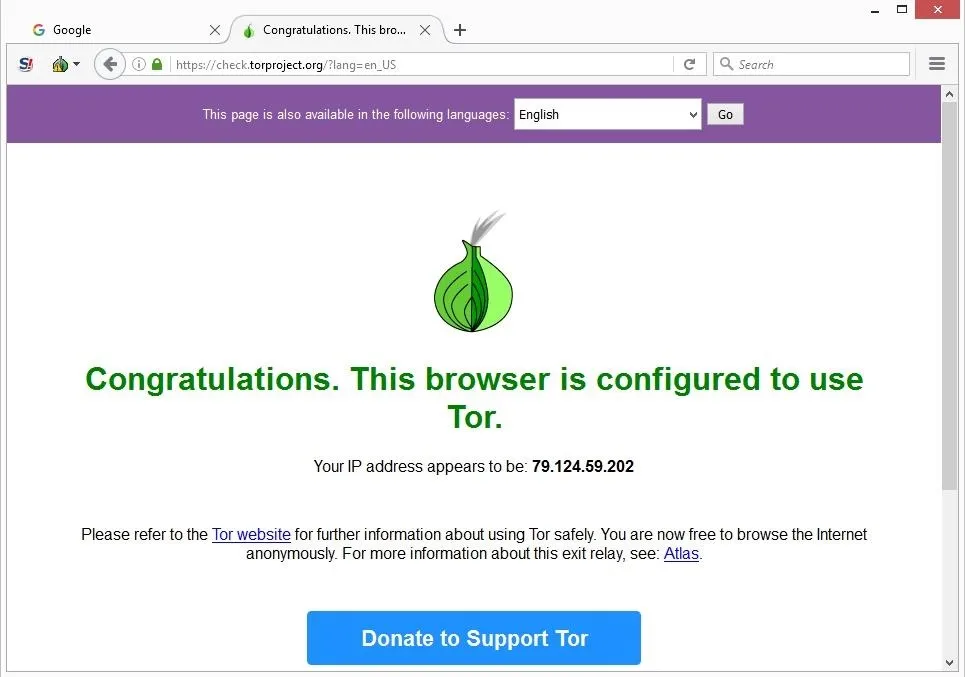
Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser. Some use similar services such as I2P, for example the Silk Road Reloaded. The visitor has to use the same encryption tool as the site and – crucially – know where to find the site, in order to type in the URL and visit. Almost all sites on the so-called Dark Web hide their identity using the Tor encryption tool.
Connect To The Tor Network

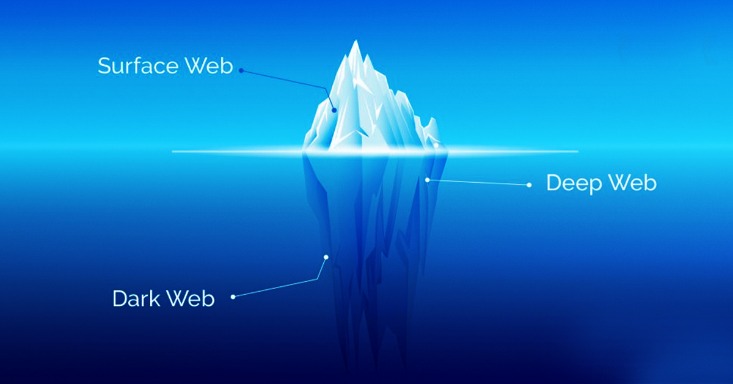
The deep web refers to any web content that is not indexed or pages that can’t be found with a search engine. Examples of the deep web include any websites that are behind a paywall or require login credentials. Most internet users access the deep web several times a day to perform common tasks, such as checking email, accessing a bank account, or reviewing health or school records. The deep web constitutes over 90% of online content and is inaccessible via search engines.
What Is The Dark Web? + 6 Tips To Access It Safely
Note that most dark web transactions are carried out using Bitcoin or other cryptocurrencies. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. Also, you must log in or have a specific IP address or URL to access the deep web content.
How To Access Dark Web?
While it has its dangers, it also serves as a hub for privacy-focused communications and access to resources. However, stepping into this part of the internet without preparation can expose you to risks. However, the line is drawn at what you’re doing once you’re on the dark web. Engaging in illegal activities—like buying drugs, trafficking stolen data, or distributing harmful content—is absolutely against the law. If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime.
- Outside or inside Tor, your traffic is secured 100% of the time.
- My favorite antivirus in 2025 is Norton, which scored a 100% protection rating during my tests (handily beating the built-in protections on my devices).
- Once again, this isn’t as secure as the Tor Browser, and your browsing information, including your IP address, might be exposed to any servers you connect to.
- While the dark web is often depicted as an anarchic forum for criminal activity, that’s not necessarily true.
- Other search engines like Haystak boast millions of indexed pages and advanced filtering options.
No Protection Against Malware
In fact, there have been instances where attackers controlled hundreds of Tor nodes. Though there are other ways to access onion websites, it is recommended that you always use Tor to access dark web websites. It offers better speed and security than other alternative methods. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. Platforms like SecureDrop even allow journalists to receive tips anonymously. The dark web hosts various types of illegal content, such as stolen data, child exploitation material, and prohibited items.
Accessing The Dark Web Without Tor: Setting Up I2P And Hyphanet
Opt for curated sources like Dark.Fail (PGP-verified mirrors) and Ahmia (filters abuse). Treat Hidden Wiki with caution and verify any link via multiple sources. Fake sites are everywhere, and even a one-character difference in the URL can land you on a phishing page.
Use A Trusted VPN
Whether you’re a journalist, an activist, or simply curious, take the necessary precautions to remain secure. The hidden web (also known as the deep web or deep net) is the largest part of the internet. It comprises websites that aren’t easily accessible mainly because they are non-indexed, password-protected or paywalled. The dark web is a small subset of the deep web comprising purely non-indexed websites and services.
Navigating the Dark Web offers anonymity and freedom, but it also comes with significant risks that can jeopardize both individuals and organizations. Hidden websites often harbor malicious software designed to steal sensitive information, infect devices, or even deploy ransomware. A single careless click can compromise your entire digital ecosystem. A VPN adds that extra layer of privacy you need when browsing the dark web on Tor.
How To Access The Dark Web Using The Tor Browser?
Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. The Deep Web forms a more expansive but hidden layer beyond the reach of conventional search engines.
It will still be able to get the job done if you’re interested in dark web browsing. Apps are independently audited for security and are available for Windows, macOS, Linux, iOS, and Android. Connection speeds are very fast, and you should be able to stream HD and 4K content without buffering. Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+. NordVPN is offering a fully-featured risk-free day trial if you sign up at this page .
I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users. It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. Freenet is a decentralized, peer-to-peer platform designed for the secure and anonymous sharing of information over the Internet. It focuses on privacy, censorship resistance, and ensuring free access to content. To access the Freenet-based dark web, you need to install the Freenet application. The dark web, a subset of the deep web, cannot be accessed with a regular browser.
Step 2: Download And Verify The Tails OS Image
- Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android.
- These are the final stops in the Tor relay chain before your traffic hits the open web.
- Each of these options offers unique privacy features, with Whonix and Qubes for higher security setups, and Kodachi and Liberté for portability.
- Using a VPN in conjunction with the Tor (The Onion Router) browser is the best way to access the dark web safely.
- This makes it extremely difficult to find out who you are transacting with.
With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents. The dark web — aka, the deep web — is the second layer of the internet, which is not indexed by search engines. Websites and pages in the deep web might include password-protected content, private forums, and personalized resources.
For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question. If the VPN connection fails, the automatic kill switch will kick in, temporarily breaking your traffic. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. For this reason, you must watch out and avoid opening anything that looks suspicious to you. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user.
You can use the VPN rated #1 with no restrictions for a month – great if you want to binge your favorite show or are going on a short trip. We’ll get into more detail about individual providers later in this article. If any link looks weird, it likely is and may be a phishing link. Don’t open attachments from untrusted sources, as they are a common vector for spreading malware. For example, in Safer mode, JavaScript is turned off on non-HTTPS (insecure) sites, but in Safest mode, JavaScript is turned off entirely for all sites. Images load normally in Safer mode, but some complex images may not load in Safest mode.



