In the next sections, we will focus on the steps you can take to access the Dark Web on your Android device safely and responsibly. Our marketplace offers a diverse range of products, ensuring secure and private transactions for all users. However, many activities that take place on the darknet are illegal, and you should be aware of this before accessing it. People mostly use it for covert communication, anonymous tips submission, and stuff like that.
- This article will provide a comprehensive guide on how to access the darknet on Android devices.
- Good antivirus software (like Norton) helps detect and block these threats, providing an extra layer of security when accessing the dark web.
- The Darknet is an intriguing but often misunderstood aspect of the internet.
- Protect your device with updated software and antivirus measures, and always be conscious of the information you share.
- Several sites hosting illegal material have been discovered by government agencies and shut down in recent years, including Silk Road, AlphaBay, and Hansa.
Facilitates Discreet Internet Use
The dark web is undoubtedly dangerous, but it can also create a lot of good for the world. It’s useful for research, helping journalists shed light on injustice, communicating anonymously, and investigating criminal activity. Tor over VPN directs your traffic through the VPN server before going through Tor’s network — while VPN over Tor directs your traffic through Tor’s browser first. For Chromebook users — unfortunately, there isn’t an official Tor app available for ChromeOS at this time. Several sites hosting illegal material have been discovered by government agencies and shut down in recent years, including Silk Road, AlphaBay, and Hansa.
Using a different browser than these could put your privacy at serious risk and could expose you to attacks from cybercriminals. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Great life advice, but it’s even more valuable where the darknet is concerned. Keep in mind that many criminal organizations use the dark web to communicate or sell merchandise. You may very well end up in the middle of a stakeout that could turn ugly.
How To Get On The Dark Web: A Step-by-Step Guide
- By following the steps outlined and adhering to safety measures, users can explore the darknet more securely.
- Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites.
- However, if you decide to use a burner phone and intend to browse the dark web, we recommend using a no-logs VPN to conceal your Tor activity from your ISP and hide your real IP address.
- Utilize tools like Tor, Orbot, Onion Browser, and VPNs to maintain anonymity.
- Also, the bad actors can use tools like keyloggers to gather data and infiltrate your system.
By completing these preparations, you can ensure that your Android device is in a secure and optimal state for accessing the Dark Web. Remember, it’s essential to prioritize your security and privacy throughout this process. Therefore, before embarking on your journey to explore the Dark Web, it is crucial to familiarize yourself with the legal implications and the risks involved.
How To Sell Counter-Strike 2 Skins Instantly? A Comprehensive Guide
Knowing how to access darknet Android responsibly allows you to take advantage of its benefits while minimizing risks. Always prioritize your online security and be aware of the legal parameters surrounding your activities. While accessing the Deep Web, users might come across a lot of lucrative deals and attractive links, but all of them are basically traps.

When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web.
A Beginner’s Guide To The Dark Web And Online Anonymity

While there’s no official Tor iOS app, other apps, such as Onion browser, are free. You need a specialized browser, like Onion browser, to access the dark web on iPhone. You could also use NordVPN’s Onion Over VPN and visit the dark web on any browser, like Safari. NordVPN uses industry-leading encryption to secure your browsing activity.
What’s The Difference Between Tor Over VPN And VPN Over Tor?
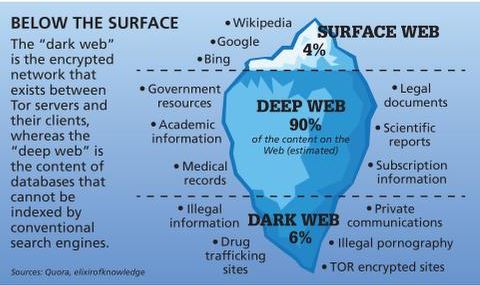
However, there are also many legitimate uses for the darknet, such as protecting privacy, free speech, and whistleblowing. Dark web search engines and forums like Reddit can help you find reliable dark websites, and you’ll need to use a dark web browser to visit them. The dark web — aka, the deep web — is the second layer of the internet, which is not indexed by search engines. Websites and pages in the deep web might include password-protected content, private forums, and personalized resources. One of the first lines of defense is using a Virtual Private Network, or VPN.

Installing A Virtual Machine On Your Phone
As long as users take the necessary precautions, no one knows who anyone else is in the real world. Users’ identities are safe from the prying eyes of governments and corporations. The dark web, or dark net, is a small part of the deep web that is kept hidden on purpose. Websites and data on the dark web do typically require a special tool to access. Our rigorous research and testing have revealed revealing truths and busted myths.
Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network. Then, simply click the operating system that you are using and download the file.
ExpressVPN is my favorite VPN for browsing pages on the dark web in 2024 — it supports Tor traffic, provides excellent security and privacy features, and has very fast speeds. This site lets you access public texts of court decisions from around the world. Accessing the Dark Web does carry risks of being traced, tracked, or hacked, particularly if security measures are not adequately followed. While the Tor network provides a level of security, vulnerabilities can still expose you to cyber threats. To minimize these risks, it’s crucial to follow best practices for security while accessing the Dark Web, including the use of VPNs. A VPN’s encryption is particularly key in protecting the connection between your device and the first Tor relay (entry node).

The official Tor browser isn’t available for iOS, and you need to use two different apps to get into the Dark Web. I’m using the Onion Browser, which is from the Tor Project, along with Orbot to connect to the Tor network. Before starting Tor Browser, it’s recommended to use a VPN for an added layer of security. A VPN encrypts your internet traffic and hides your IP address, providing an extra level of privacy.
However, your online activity is encrypted and hidden from view thanks to Tor’s onion routing. This means your ISP can’t see that you’re accessing the dark web (or indeed, the specific sites you’re accessing). The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity. Unlike the regular internet, the dark web doesn’t use standard URLs or search engines. Instead, sites have complex .onion addresses, making them difficult to find without the exact URL.
How To Access The Dark Web On Phone
Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that). So, do yourself a favor and rescale that Tor window as much as you can before proceeding. We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those. Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. Note that the process can take anywhere from 5 to 30 minutes depending on your machine. This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity.



