Before you embark on your journey into the Dark Web, it’s crucial to establish a secure foundation. While the Tor network is designed to provide anonymity, it alone cannot guarantee your privacy or safety. This section will guide you through the essential preparatory steps and tools to ensure that you remain as protected as possible while exploring hidden services and tor onion domains. The “Dark Web” often conjures up images of hidden marketplaces, illicit trades, and shadowy figures lurking in the digital underworld. The Dark Web is simply a part of the internet that cannot be reached by standard search engines and browsers.
Want To Browse Anonymously?
The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect. The moderation team likely has no connections or relationships with individuals or organizations who sell, buy, and post in r/darknet, have a connection to r/darknet, or to the dark web. We cannot help you resolve conflicts stemming from your private dealings with people inside or outside of this subreddit. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
Step-by-Step Guide: How To Access The Dark Web Using Tor Browser
Use VPN, avoid logging into personal accounts, enable Tor security settings, and stick to trusted sites. Download the Linux version from torproject.org, extract the file, and run the start-tor-browser script. While difficult, tracking is possible if security measures are misconfigured or if users reveal personal information. Combining it with VPN and good digital hygiene improves security. Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity.

Detailed Steps To Access The Dark Web Using Tor
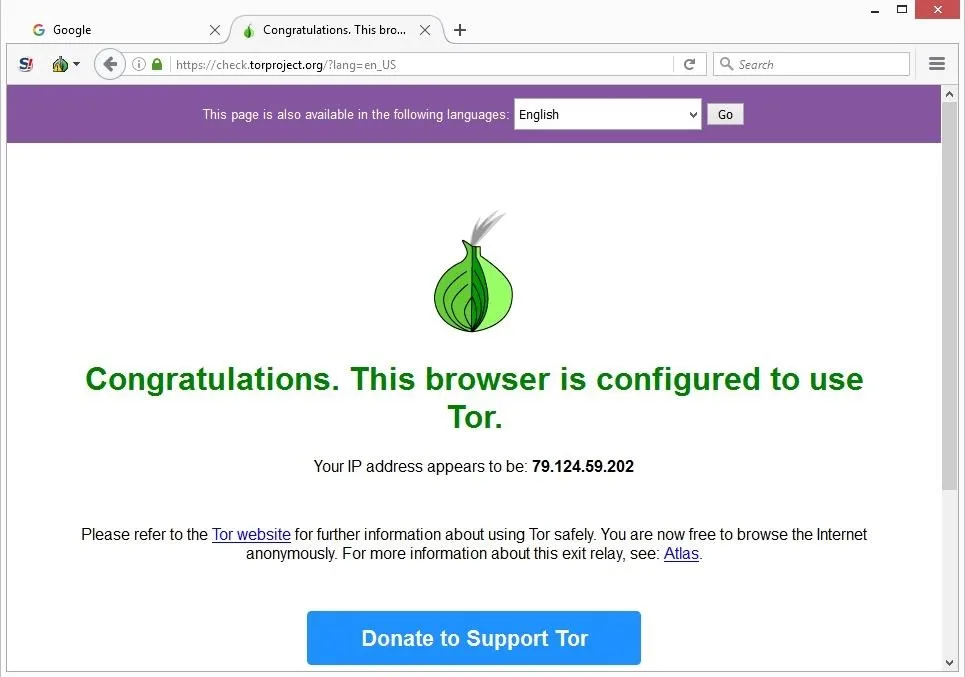
If you want to be untraceable and undetectable, connecting to the dark web via the Tor browser is a major step towards that, but not the only step you’ll need. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
How Do I Recognize Phishing Sites On The Dark Web?
Well-known news websites, such as ProPublica, have launched deep websites. Meanwhile, Facebook also offers dark web access to their social network. The deep web is made up of content that search engines such as Google do not index. Such data includes medical records, financial information, research papers, private forums and networks, and other content. The top layer is referred to as the clear or “surface web,” which is what you’re accessing while reading this article. The clear web is made up of websites that you can get to via a search engine like Ecosia or Google.
The Best Dark Web Search Engines In 2024
Specialized search engines, directories, and wikis can help users locate the data they’re looking for. Because dark web pages generally aren’t indexed, you can’t find them using traditional search engines, but some search engines like DuckDuckGo may help you navigate the dark web more easily. The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites. While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. The deep web is the next layer, and it encompasses a massive amount of online data that is not available for public consumption and not indexed by clear web search engines. Deep web content includes academic research papers, court documents, or medical records.
What Is APKPure And Is It Safe To Use On Android?
It collects data from the public Tor network and archives historical data of the Tor ecosystem. Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see. For example, it has a reputation for hosting pedophile sites. It is an excellent option if you want to surf the web anonymously.

Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. The early version of Tor was created to mask spy communications.
Think of Tor as a regular browser like Firefox, Google, or Safari. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed.
The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access.

Specialized Operating Systems: Whonix And Tails
Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. That information can include checking and credit card account numbers, social security numbers, and other sensitive information. Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy.
The technology behind this anonymous connection is known as “onion routing,” which utilizes a layered approach to obscure data and protect users’ locations on the network. After all, it’s much less popular, can’t be used to access normal websites, and isn’t as easy to use, among other disadvantages. Both rely on a peer-to-peer routing structure and layered encryption to make browsing private and anonymous. Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites. VPN over Tor requires you to place trust in your ISP but not your VPN and is best if you want to avoid bad Tor exit nodes. Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously).
- Believe me – there are plenty to go around and each and every one of them are being kept under surveillance.
- For instance, the Ashley Madison data dump was posted to a site only accessible to Tor users.
- Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later.
- Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
- That means that only 0.024% of all the known pages are findable in Google’s search engine.
The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. On the deep web, you can find such “private” information on web pages.
#2 Install An Adequate Browser
For example, when you sign in to your healthcare provider’s portal to view test results or request prescription refills, you’re accessing the deep web. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. You don’t need special tools or a special browser like you need to access the dark web (more about that later).



